Based on real data, the CompTIA CySA+ CS0-002 dumps makes the exam 100% easier. So we’ve prepared 12 free exam questions for you from the Pass4itSure CS0-002 dumps.
For more click here https://www.pass4itsure.com/cs0-002.html CompTIA CySA+ CS0-002 dumps PDF+VCE Q&As: 769.

Read on:
- 12 free CompTIA Cybersecurity Analyst (CySA+) practice questions
- The latest update google drive CS0-002 pdf
- Advice on how to best achieve CS0-002 exam success
12 free CompTIA Cybersecurity Analyst (CySA+) practice questions:
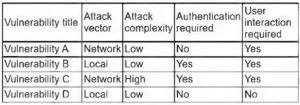
CS0-002 q1.
Ransomware is identified on a company\\’s network that affects both Windows and MAC hosts. The command and control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1.
Iholdbadkeys.com, which resolves to IP address 72.172.16.2. Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?
A. block all outbound traffic to web host good1 iholdbadkeys.com at the border gateway.
B. Block all outbound TCP connections to IP host address 172.172.16.2 at the border gateway.
C. Block all outbound traffic on TCP ports 11000 to 65000 at the border gateway.
D. Block all outbound traffic on TCP ports 11000 to 65000 to IP host address 172.172.16.2 at the border gateway.
Correct Answer: A
CS0-002 q2.
An organization wants to mitigate against risks associated with network reconnaissance. ICMP is already blocked at the firewall; however, a penetration testing team has been able to perform reconnaissance against the organization\\’s network and identify active hosts. An analyst sees the following output from a packet capture:

Which of the following phrases from the output provides information on how the testing team is successfully getting around the ICMP firewall rule?
A. flags=RA indicates the testing team is using a Christmas tree attack
B. ttl=64 indicates the testing team is setting the time to live below the firewall\\’s threshold
C. 0 data bytes indicate the testing team is crafting empty ICMP packets
D. NO FLAGS are set indicates the testing team is using hoping
Correct Answer: D
CS0-002 q3.
An analyst is searching a log for potential credit card leaks. The log stores all data encoded in hexadecimal. Which of the following commands will allow the security analyst to confirm the incident?
A. cat log xxd -r -p | egrep \’ [0-9] {16}
B. egrep \'(3(0-9)) (16) \’ log
C. cat log | xxd -r -p egrep \'(0-9) (16)\’
D. egrep \’ (0-9) (16) \’ log | xxdc
Correct Answer: C
CS0-002 q4.
A SIEM solution alerts a security analyst of a high number of login attempts against the company\\’s webmail portal. The analyst determines the login attempts used credentials from a past data breach.
Which of the following is the BEST mitigation to prevent unauthorized access?
A. Single sign-on
B. Mandatory access control
C. Multifactor authentication
D. Federation
E. Privileged access management
Correct Answer: E
CS0-002 q5.
A small organization has proprietary software that is used internally. The system has not been well maintained and cannot be updated with the rest of the environment Which of the following is the BEST solution?
A. Virtualize the system and decommission the physical machine.
B. remove it from the network and require air gapping.
C. Only allow access to the system via a jump box
D. Implement MFA on the specific system.
Correct Answer: A
CS0-002 q6.
A cybersecurity analyst is responding to an incident. The company\’s leadership team wants to attribute the incident to an attack group. Which of the following models would BEST apply to the situation?
A. Intelligence cycle
B. Diamond Model of Intrusion Analysis
C. Kill chain
D. MITRE ATTandCK
Correct Answer: B
CS0-002 q7.
Which of the following BEST describes the primary role of a risk assessment as it relates to compliance with risk-based frameworks?
A. It demonstrates the organization\\’s mitigation of risks associated with internal threats.
B. It serves as the basis for control selection.
C. It prescribes technical control requirements.
D. It is an input to the business impact assessment.
Correct Answer: A
CS0-002 q8.
A security analyst receives a CVE bulletin, which lists several products that are used in the enterprise. The analyst immediately deploys a critical security patch. Which of the following BEST describes the reason for the analyst\\’simmediate action?
A. Nation-state hackers are targeting the region.
B. A new vulnerability was discovered by a vendor.
C. A known exploit was discovered.
D. A new zero-day threat needs to be addressed.
E. There is an insider threat.
Correct Answer: B
CS0-002 q9.
An organization recently discovered a malware sample on an internal server. IoCs showed the malware sample was
running on port 27573.
The incident response team successfully removed the malware from the server, but the organization is now concerned about other instances of the malware being installed on another server.
The following network traffic was captured after the known malware was assumed to be eradicated:
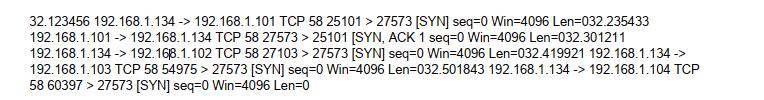
Which of the following can the organization conclude?
A. The malware was installed on servers 192.168.1.102, 192.168.1.103, and 192.168.1.104.
B. Only the server at 192.168.1.103 has an indication of a possible compromise.
C. Only the server at 192.168.1.104 has an indication of a possible compromise.
D. Both servers 192.168.1.101 and 192.168.1.134 indicate a possible compromise.
E. The server at 192.168.1.134 is exfiltrating data in 25KB files to servers throughout the organization.
Correct Answer: D
CS0-002 q10.
A cybersecurity analyst is dissecting an intrusion down to the specific techniques and wants to organize them in a logical manner. Which of the following frameworks would BEST apply in this situation?
A. Pyramid of Pain
B. MITRE ATTandCK
C. Diamond Model of Intrusion Analysts
D. CVSS v3.0
Correct Answer: B
CS0-002 q11.
Which of the following secure coding techniques can be used to prevent cross-site request forgery attacks?
A. Input validation
B. Output encoding
C. Parameterized queries
D. Tokenization
Correct Answer: D
CS0-002 q12.
While planning segmentation for an ICS environment, a security engineer determines IT resources will need access to devices within the ICS environment without compromising security.
To provide the MOST secure access model in this scenario, the jump box should be __________.
A. placed in an isolated network segment, authenticated on the IT side, and forwarded into the ICS network.
B. placed on the ICS network with a static firewall rule that allows IT network resources to authenticate.
C. bridged between the IT and operational technology networks to allow authenticated access.
D. placed on the IT side of the network, authenticated, and tunneled into the ICS environment.
Correct Answer: D
The latest update [google drive] CS0-002 pdf:
Download – free CompTIA CS0-002 dumps pdf https://drive.google.com/file/d/12ee1ZNoIIpVQxNA5fcgWvSW-Z5q0tffp/view?usp=sharing
Advice on how to best achieve CS0-002 exam success:
How to do: See the free CS0-002 exam practice test above to constantly check for any questions you made wrong on the practice exam. The next step is to get the full Pass4Sure CS0-002 dumps https://www.pass4itsure.com/cs0-002.html (769 questions) research learning.
Note: Don’t get lost, believe in yourself. It’s important to keep a good mindset. A real CS0-002 dump can effectively help you prepare to pass the CompTIA CySA+ exam.