Want to know what are the advantages of CS0-003 exam preparation? This tells you that you need valid preparation materials to pass the CySA+ CS0-003 exam, which you can get from CompTIA CySA+ CS0-003 dumps 2024. Newly updated!
Pass4itSure is strong in providing valid CS0-003 dumps that will ensure that you succeed in the actual exam. You can download Pass4itSure CS0-003 dumps 2024 https://www.pass4itsure.com/cs0-003.html (Choose from three plans: PDF, VCE, or Premium Program: Silver Premium Program, Gold Premium Program, and Diamond Premium Program.) Choose the right one according to your needs.
For the Premium Program, you can get details here.
I won’t introduce the basic content of the exam here, I believe everyone has already understood. Mainly share the latest learning resources about the CySA+ CSO-003 exam.
Significant changes to the CS0-003 exam
Each update brings new exam objectives, concepts, and techniques to the exam.
The biggest change in CS0-003 is the introduction of cloud infrastructure and web application testing tools and technologies.
Compared with CS0-002, the number of CS0-003 exam objectives has been reduced from five to four
- Secure operations
- Vulnerability management
- Incident response and management
- Reporting and Communication
These changes are huge, and everyone must pay attention to grasp the key points of the exam. Only by grasping the key points of the exam can you easily pass the CS0-003 exam.
The exam you know: CySA+ CSO-003
There are two exams (CS0-002 & CS0-003) for the CompTIA CySA+ certification, one of which is CSO-003. It is a certification for networking professionals.
CompTIA CySA+ (CS0-002) has been retired on December 5, 2023. So now the CS0-003 exam is the mainstream.
Mike Chapple shared that the new CS0-003 exam features were introduced, and I thought it was very good, so I would like to share it with you to learn together.
Continue the topic and share the latest CS0-003 exam questions, free, free, free.
Free CS0-003 dumps exam questions to share online
Come from: Pass4itSure
Number of Questions: 1-15
Relevant certifications: CompTIA CySA+
More CompTIA Exam Questions…
Question 1:
A security analyst discovers the accounting department is hosting an accounts receivable form on a public document service. Anyone with the link can access it. Which of the following threats applies to this situation?
A. Potential data loss to external users
B. Loss of public/private key management
C. Cloud-based authentication attack
D. Identification and authentication failures
Correct Answer: A
Potential data loss to external users is a threat that applies to this situation, where the accounting department is hosting an accounts receivable form on a public document service. Anyone with the link can access it. Data loss is an event that results in the destruction, corruption, or unauthorized disclosure of sensitive or confidential data.
Data loss can occur due to various reasons, such as human error, hardware failure, malware infection, or cyberattack. In this case, hosting an accounts receivable form on a public document service exposes the data to potential data loss to external users who may access it without authorization or maliciously modify or delete it.
Question 2:
A SOC analyst recommends adding a layer of defense for all endpoints that will better protect against external threats regardless of the device\’s operating system. Which of the following best meets this requirement?
A. SIEM
B. CASB
C. SOAR
D. EDR
Correct Answer: D
EDR stands for Endpoint Detection and Response, which is a layer of defense that monitors endpoints for malicious activity and provides automated or manual response capabilities. EDR can protect against external threats regardless of the device\’s operating system, as it can detect and respond to attacks based on behavioral analysis and threat intelligence. EDR is also one of the tools that CompTIA CySA+ covers in its exam objective
https://www.comptia.org/certifications/cybersecurity-analyst https://www.comptia.org/blog/the-new-comptia-cybersecurity-analyst-your-questions-answered
Question 3:
A security analyst must preserve a system hard drive that was involved in a litigation request
Which of the following is the best method to ensure the data on the device is not modified?
A. Generate a hash value and make a backup image.
B. Encrypt the device to ensure confidentiality of the data.
C. Protect the device with a complex password.
D. Perform a memory scan dump to collect residual data.
Correct Answer: A
Generating a hash value and making a backup image is the best method to ensure the data on the device is not modified, as it creates a verifiable copy of the original data that can be used for forensic analysis.
Encrypting the device, protecting it with a password, or performing a memory scan dump does not prevent the data from being altered or deleted. Verified References: CompTIA CySA+ CS0-002 Certification Study Guide, page 3291
Question 4:
An organization\’s threat intelligence team notes a recent trend in adversary privilege escalation procedures. Multiple threat groups have been observed utilizing native Windows tools to bypass system controls and execute commands with privileged credentials. Which of the following controls would be most effective to reduce the rate of success of such attempts?
A. Set user account control protection to the most restrictive level on all devices
B. Implement MFA requirements for all internal resources
C. Harden systems by disabling or removing unnecessary services
D. Implement controls to block the execution of untrusted applications
Correct Answer: C
Question 5:
An organization has the following risk mitigation policies
Risks without compensating controls will be mitigated first if the nsk value is greater than $50,000 Other nsk mitigation will be hypnotized based on risk value.
The following risks have been identified: Which of the following is the order of priority for risk mitigation from highest to lowest?
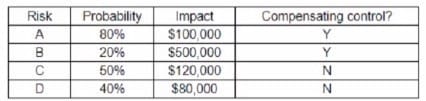
A. A, C, D, B
B. B, C, D, A
C. C, B, A, D
D. C. D, A, B
E. D, C, B, A
Correct Answer: C
The order of priority for risk mitigation from highest to lowest is C, B, A, D. This order is based on applying the risk mitigation policies of the organization. According to the first policy, risks without compensating controls will be mitigated first if the risk value is greater than $50,000.
Risk C has no compensating controls and a risk value of $75,000, so it is the highest priority. Risk B also has no compensating controls, but a risk value of $40,000, so it is the second priority. According to the second policy, other risk mitigation will be prioritized based on risk value.
Risk A has a risk value of $60,000 and a compensating control of encryption, so it is the third priority. Risk D has a risk value of $50,000 and a compensating control of the backup power supply, so it is the lowest priority.
Question 6:
An analyst needs to understand how an attacker compromised a server. Which of the following procedures will best deliver the information that is necessary to reconstruct the steps taken by the attacker?
A. Scan the affected system with an anti-malware tool and check for vulnerabilities with a vulnerability scanner.
B. Extract the server\’s system timeline, verifying hashes and network connections during a certain time frame.
C. Clone the entire system and deploy it in a network segment built for tests and investigations while monitoring the system during a certain time frame.
D. Clone the server\’s hard disk and extract all the binary files, comparing hash signatures with malware databases.
Correct Answer: B
Question 7:
An analyst is remediating items associated with a recent incident. The analyst has isolated the vulnerability and is actively removing it from the system. Which of the following steps of the process does this describe?
A. Eradication
B. Recovery
C. Containment
D. Preparation
Correct Answer: A
Eradication is a step in the incident response process that involves removing any traces or remnants of the incident from the affected systems or networks, such as malware, backdoors, compromised accounts, or malicious files.
Eradication also involves restoring the systems or networks to their normal or secure state, as well as verifying that the incident is eliminated and cannot recur. In this case, the analyst is remediating items associated with a recent incident by isolating the vulnerability and actively removing it from the system. This describes the eradication step of the incident response process.
Question 8:
A risk assessment concludes that the perimeter network has the highest potential for compromise by an attacker, and it is labeled as a critical risk environment. Which of the following is a valid compensating control to reduce the volume of valuable information in the perimeter network that an attacker could gain using active reconnaissance techniques?
A. A control that demonstrates that all systems authenticate using the approved authentication method
B. A control that demonstrates that access to a system is only allowed by using SSH
C. A control that demonstrates that firewall rules are peer-reviewed for accuracy and approved before deployment
D. A control that demonstrates that the network security policy is reviewed and updated yearly
Correct Answer: C
A valid compensating control to reduce the volume of valuable information in the perimeter network that an attacker could gain using active reconnaissance techniques is a control that demonstrates that firewall rules are peer-reviewed for accuracy and approved before deployment.
This control can help ensure that the firewall rules are configured correctly and securely and that they do not allow unnecessary or unauthorized access to the perimeter network. The other options are not compensating controls or do not address the risk of active reconnaissance. CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0-002), page 14; https://www.isaca.org/resources/isaca-journal/issues6/volume-3/compensating-controls
Question 9:
A company that has a geographically diverse workforce and dynamic IPs wants to implement a vulnerability scanning method with reduced network traffic. Which of the following would best meet this requirement?
A. External
B. Agent-based
C. Non-credentialed
D. Credentialed
Correct Answer: B
Agent-based vulnerability scanning is a method that involves installing software agents on the target systems or networks that can perform local scans and report the results to a central server or console. Agent-based vulnerability scanning can reduce network traffic, as the scans are performed locally and only the results are transmitted over the network.
Agent-based vulnerability scanning can also provide more accurate and up-to-date results, as the agents can scan continuously or on-demand, regardless of the system or network status or location.
Question 10:
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques. Which of the following would best mitigate such attacks?
A. Keeping IPS rules up to date
B. Installing a proxy server
C. Applying network segmentation
D. Updating the antivirus software
Correct Answer: A
Question 11:
An organization wants to move non-essential services into a cloud computing environment. The management team has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work best to attain the desired outcome?
A. Duplicate all services in another instance and load balance between the instances.
B. Establish a hot site with active replication to another region within the same cloud provider.
C. Set up a warm disaster recovery site with the same cloud provider in a different region.
D. Configure the systems with a cold site at another cloud provider that can be used for failover.
Correct Answer: C
Setting up a warm disaster recovery site with the same cloud provider in a different region can help to achieve a recovery time objective (RTO) of 12 hours while keeping the costs low. A warm disaster recovery site is a partially configured site that has some of the essential hardware and software components ready to be activated in case of a disaster.
A warm site can provide faster recovery than a cold site, which has no preconfigured components but has lower costs than a hot site, which has fully configured and replicated components. Using the same cloud provider can help to simplify the migration and synchronization processes while using a different region can help to avoid regional outages or disasters. https://www.techopedia.com/definition39/memory-dump
Question 12:
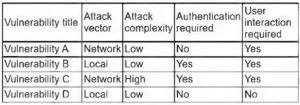
A recent zero-day vulnerability is being actively exploited, requires no user interaction or privilege escalation, and has a significant impact on confidentiality and integrity but not on availability. Which of the following CVE metrics would be most accurate for this zero-day threat?
A. CVSS: 31/AV: N/AC: L/PR: N/UI: N/S: U/C: H: K/A: L
B. CVSS:31/AV:K/AC:L/PR:H/UI:R/S:C/C:H/I:H/A:L
C. CVSS:31/AV:N/AC:L/PR:N/UI:H/S:U/C:L/I:N/A:H
D. CVSS:31/AV:L/AC:L/PR:R/UI:R/S:U/C:H/I:L/A:H
Correct Answer: A
This answer matches the description of the zero-day threat. The attack vector is network (AV: N), the attack complexity is low (AC:L), no privileges are required (PR: N), no user interaction is required (UI: N), the scope is unchanged (S: U), the confidentiality and integrity impacts are high (C:H/I: H), and the availability impact is low (A:L). Official https://nvd.nist.gov/vuln-metrics/cvss
Question 13:
Joe, a leading salesperson at an organization, has announced on social media that he is leaving his current role to start a new company that will compete with his current employer. Joe is soliciting his current employer\’s customers. However, Joe has not resigned or discussed this with his current supervisor yet. Which of the following would be the best action for the incident response team to recommend?
A. Isolate Joe\’s PC from the network
B. Reimage the PC based on standard operating procedures
C. Initiate a remote wipe of Joe\’s PC using mobile device management
D. not act until HR or legal counsel advises on the next steps
Correct Answer: D
The best action for the incident response team to recommend in this scenario is to not act until HR or legal counsel advises on the next steps. This action can help avoid any potential legal or ethical issues, such as violating employee privacy rights, contractual obligations, or organizational policies.
This action can also help ensure that any evidence or information collected from the “of any legal action or dispute. The incident response team should consult with HR or legal counsel before taking any action that may “
Question 14:
A security officer needs to find a solution to the current data privacy and protection gap found in the last security assessment. Which of the following is the most cost-effective solution?
A. Require users to sign NDAs.
B. Create a data minimization plan.
C. Add access control requirements.
D. Implement a data loss prevention solution.
Correct Answer: B
Question 15:
Which of the following is the BEST option to protect a web application against CSRF attacks?
A. Update the web application to the latest version.
B. Set a server-side rate limit for CSRF token generation.
C. Avoid the transmission of CSRF tokens using cookies.
D. Configure the web application to only use HTTPS and TLS 1.3.
Correct Answer: C
CSRF tokens are random values that are generated by the server and included in requests that perform state-changing actions. They are used to prevent CSRF attacks by verifying that the request originates from a legitimate source.
However, if the CSRF tokens are transmitted using cookies, they are vulnerable to being stolen or forged by an attacker who can exploit other vulnerabilities, such as cross-site scripting (XSS) or cookie injection. Therefore, a better option is to avoid the transmission of CSRF tokens using cookies and use other methods, such as hidden form fields or custom HTTP headers.
CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0-002), page 11; https:// owasp.org/www-community/attacks/csrf
And much more, for you to prepare the CSO-003 exam study resources (latest) in various forms.
CSO-003 exam study resources package (with link) 2024
Document format:
- CompTIA CySA+ CS0-003 Certification Study Guide
- Apply your knowledge with CertMaster Labs
- Practice and prepare for your exam with CertMaster Practice
- CertMaster Practice for CySA+ Training
Book format:
You may still have these questions about the exam, and we have answered them for you.
Questions about CySA+ CSO-003 exam
Now, should I choose CySA CSO-002 or CSO-003?
Must be CSO-003, CySA CSO-002 is retired.
What should I do if the CySA+ CSO-003 exam feels very difficult?
The method of preparing for the exam is incorrect. You can try Pass4itSure CySA+ CS0-003 Dumps 2024 to prepare.
Which is the first choice for Security+ or CySA+ certification?
CySA+ is an intermediate-level credential, slightly higher than CompTIA’s entry-level Security+ certification. If you don’t have a foundation at first, you should start with Security+.
Write at the end:
Take advantage of CySA+ CS0-003 exam preparation – Get the CS0-003 Dumps 2024 to prepare for the exam with ease and win ahead.
Get CS0-003 dumps 2024 https://www.pass4itsure.com/cs0-003.html Choose from three plans, PDF, VCE, or Premium Program) and then brush up on the questions and finally win the exam.
In conclusion, CS0-003 dumps 2024 is your prep advantage!
Waiting for the good news that you have successfully passed the exam.