It doesn’t matter if you don’t get a high score in the SY0-601 mock exam, you get a high score in the final exam! Of course, if you get a high score on a mock exam, it also means that you are proficient in CompTIA SY0-601 exam skills, adding points to your final CompTIA Security plus 2021 exam. Well, you need the help of the SY0-601 exam dumps.
Pass4itSure has updated the latest valid CompTIA SY0-601 exam dumps Q&A. All exam questions have been verified to ensure successful passing of the exam.
Pass4itSure SY0-601 dumps https://www.pass4itsure.com/sy0-601.html (Total Questions: 417 Q&A). With many years of exam experience.
You can experience part of the exam practice questions shared by Pass4itSure online for free.
Free CompTIA SY0-601 exam dumps pdf
Follow the link below for CompTIA SY0-601pdf: https://drive.google.com/file/d/1ypH2g4m763tSoQNhJsC5tLNzi6K-2ZM3/view?usp=sharing
Part of the SY0-601 exam practice questions
QUESTION 1 #
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.
Select and Place:
Correct Answer:
When dealing with multiple issues, address them in order of volatility (OOV); always deal with the most volatile first. Volatility can be thought of as the amount of time that you have to collect certain data before a window of opportunity is gone.
Naturally, in an investigation, you want to collect everything, but some data will exist longer than others, and you cannot possibly collect all of it once. As an example, the OOV in an investigation may be RAM, hard drive data, CDs/DVDs, and printouts.
Order of volatility: Capture system images as a snapshot of what exists, look at network traffic and logs, capture any relevant video/screenshots/hashes, record time offset on the systems, talk to witnesses and track total man-hours and expenses associated with the investigation.
References:
Dulaney, Emmett, and Chuck Easton, CompTIA Security+ Study Guide, 6th Edition, Sybex, Indianapolis, 2014, p. 453
QUESTION 2 #
An attacker is attempting, to harvest user credentials on a client\’s website. A security analyst notices multiple attempts of random usernames and passwords. When the analyst types in a random username and password. the logon screen displays the following message:
Which of the following should the analyst recommend be enabled?
A. Input validation
B. Obfuscation
C. Error handling
D. Username lockout
Correct Answer: B
QUESTION 3 #
A major political party experienced a server breach. The hacker then publicly posted stolen internal communications concerning the campaign, strategies to give the opposition party an advantage.
Which of the following BEST describes these threat actors?
A. Semi-authorized hackers
B. State actors
C. Script kiddies
D. Advanced persistent threats
Correct Answer: B
QUESTION 4 #
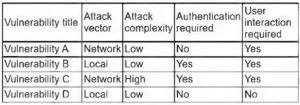
Which of the following utilize a subset of real data and are MOST likely to be used to assess the features and functions of a system and how it interacts or performs from an end user\\’s perspective against defined test cases? (Select TWO).
A. Production
B. Test
C. Research and development
D. PoC
E. UAT
F. SDLC
Correct Answer: BE
QUESTION 5 #
While reviewing the wireless router, the systems administrator of a small business determines someone is spoofing the MAC address of an authorized device. Given the table below:
Which of the following should be the administrator\\’s NEXT step to detect if there is a rogue system without impacting availability?
A. Conduct a ping sweep.
B. Physically check each system,
C. Deny Internet access to the “UNKNOWN” hostname.
D. Apply MAC filtering,
Correct Answer: D
QUESTION 6 #
A local coffee shop runs a small WiFi hotspot for its customers that utilizes WPA2-PSK. The coffee shop would like to stay current with security trends and wants to implement WPA3 to make its WiFi even more secure. Which of the following technologies will the coffee shop MOST likely use in place of PSK?
A. WEP
B. MSCHAP
C. WPS
D. SAE
Correct Answer: D
QUESTION 7 #
Drag and drop the correct protocol to its default port.
Select and Place:
Correct Answer:
Stewart, James Michael, CompTIA Security+ Review Guide, Sybex, Indianapolis, 2014, pp. 42, 45, 51
http://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
QUESTION 8 #
A multinational organization that offers web-based services has data centers that are located only in the United States; however, a large number of its customers are in Australia, Europe, and China. Payments for services are managed by a third party in the United Kingdom that specializes in payment gateways. The management team is concerned the organization is not compliant with privacy laws that cover some of its customers. Which of the following frameworks should the management team follow?
A. Payment Card Industry Data Security Standard
B. Cloud Security Alliance Best Practices
C. ISO/IEC 27032 Cybersecurity Guidelines
D. General Data Protection Regulation
Correct Answer: A
QUESTION 9 #
Which of the following BEST describes security exploit for which a vendor patch is not readily available?
A. Integer overflow
B. Zero-day
C. End of life
D. Race condition
Correct Answer: B
QUESTION 10 #
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
A. SSAE SOC 2
B. PCI DSS
C. GDPR
D. ISO 31000
Correct Answer: C
QUESTION 11 #
A security analyst is performing a forensic investigation of compromised account credentials. Using the Event Viewer, the analyst is able to detect the following message, `\\’Special privileges assigned to the new login.\\’\\’ Several of these messages did not have a valid login associated with the user before these privileges were assigned. Which of the following attacks is MOST likely being detected?
A. Pass-the-hash
B. Buffer overflow
C. Cross-site scripting
D. Session replay
Correct Answer: A
QUESTION 12 #
A Chief Security Officer (CSO) is concerned about the volume and integrity of sensitive information that is exchanged between the organization and a third party through email. The CSO is particularly concerned about an unauthorized party who is intercepting information that is in transit between the two organizations. Which of the following would address the CSO\\’s concerns?
A. SPF
B. DMARC
C. SSL
D. DKIM
E. TLS
Correct Answer: E
QUESTION 13 #
A host was infected with malware. During the incident response, Joe, a user, reported that he did not receive any emails with links, but he had been browsing the Internet all day. Which of the following would MOST likely show where the malware originated?
A. The DNS logs
B. The web server logs
C. The SIP traffic logs
D. The SNMP logs
Correct Answer: A
To get the complete CompTIA SY0-601 exam questions and answers, please choose Pass4itSure.
It doesn’t matter if you don’t get a high score on the SY0-601 mock exam, as long as you get good grades in the final exam. To get the perfect score, not only do you have to work hard to read and practice, but you also need reliable SY0-601 exam dumps to help! Pass4itSure has the most complete exam policy!
If the exam is not successful, a full refund will be given! To pass the CompTIA SY0-601 exam, click on the https://www.pass4itsure.com/sy0-601.html (PDF and VCE) to get the key to successfully passing the exam!
[Free Part] Get free SY0-601 exam PDF online: https://drive.google.com/file/d/1ypH2g4m763tSoQNhJsC5tLNzi6K-2ZM3/view?usp=sharing