The CompTIA Network+ (N10-008) Exam will be updated to the N10-009 Exam starting from June 2024. Candidates starting now to plan for CompTIA Network+ certification in 2025 and the next three years need to take the N10-009 exam. Pass4itsure has been committed to CompTIA Network+ certification solutions for many years and provides the latest CompTIA N10-009 exam practice questions in real-time: https://www.pass4itsure.com/n10-009.html, guaranteed to be actually effective.
The new Network+ (N10-009) Q&A
Candidates who have just prepared for the CompTIA Network+ certification exam will definitely have many doubts. Why is CompTIA updated every three years? In fact, This update model has been available for many years. As the latest CompTIA Network+ certification exam, CompTIA is very friendly in bringing together All the Question and Answer information to help candidates solve their doubts.
Practice the latest CompTIA N10-009 exam questions online
| From | Number of exam questions (Free Share) | Related | More |
| Pass4itsure | 15 | CompTIA exam practice questions | 263 Q&As |
Question 1:
Which of the following should be configured so users can authenticate to a wireless network using company credentials?
A. SSO
B. SAML
C. MFA
D. RADIUS
Correct Answer: D
RADIUS (Remote Authentication Dial-In User Service) is a networking protocol that provides centralized Authentication, Authorization, and Accounting (AAA) management for users who connect and use a network service. RADIUS is often used to manage access to wireless networks, enabling users to authenticate with their company credentials, ensuring secure access to the network.
References: CompTIA Network+ study materials.
Question 2:
SIMULATION You have been tasked with setting up a wireless network in an office. The network will consist of 3 Access Points and a single switch. The network must meet the following parameters: The SSIDs need to be configured as CorpNet with a key of S3cr3t! The wireless signals should not interfere with each other The subnet the Access Points and switch are on should only support 30 devices maximum The Access Points should be configured to only support TKIP clients at a maximum speed INSTRUCTONS Click on the wireless devices and review their information and adjust the settings of the access points to meet the given requirements. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
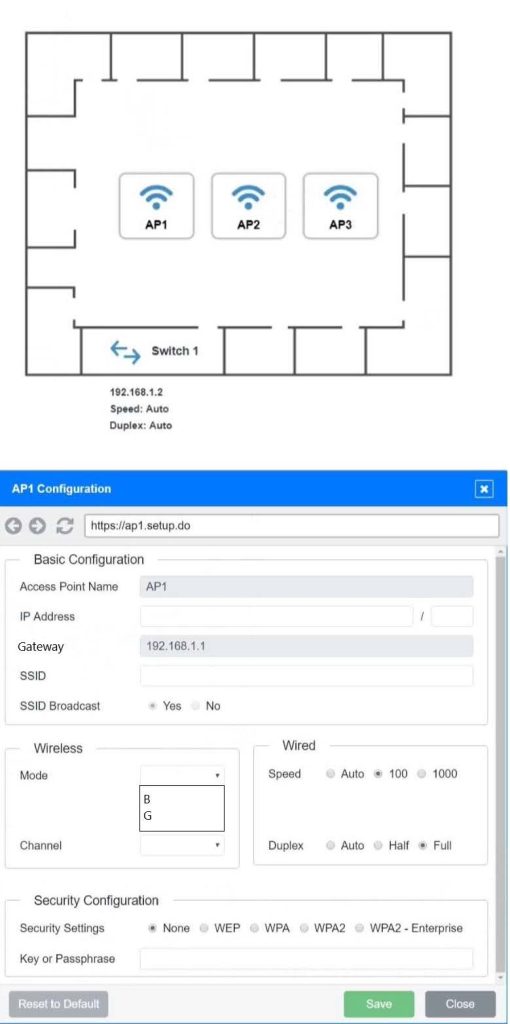
A. See explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
AP1
192.168.1.3 /27 Gateway: 192.168.1.1 Mode: G
SSD: CorpNet ** This is Case Sensitive, Whatever is on the test for SSID thats how it should be **
Key: S3cr3t!
Security Settings: WPA
Speed: Auto/Auto
AP2
192.168.1.4 /27 Gateway: 192.168.1.1 Mode: G SSD: CorpNet ** This is Case Sensitive, Whatever is on the test for SSID thats how it should be ** Key: S3cr3t! Security Settings: WPA Speed: Auto/Auto
AP3
192.168.1.5 /27 Gateway: 192.168.1.1 Mode: G SSD: CorpNet ** This is Case Sensitive, Whatever is on the test for SSID thats how it should be ** Key: S3cr3t! Security Settings: WPA Speed: Auto/Auto
192.168.1.2 Is your switch.
Question 3:
A network engineer performed a migration to a new mail server. The engineer changed the MX record, verified the change was accurate, and confirmed the new mail server was reachable via the IP address in the A record. However, users are not receiving email. Which of the following should the engineer have done to prevent the issue from occurring?
A. Change the email client configuration to match the MX record.
B. Reduce the TTL record prior to the MX record change.
C. Perform a DNS zone transfer prior to the MX record change.
D. Update the NS record to reflect the IP address change.
Correct Answer: B
TTL (Time To Live): TTL is a value in a DNS record that determines the amount of time it can be cached by DNS resolvers and other devices on the internet. When making changes to DNS records, reducing the TTL beforehand helps minimize the time it takes for the changes to propagate throughout the internet.
MX Record Change: Changing the MX (Mail Exchange) record directs email traffic to the specified mail server. However, DNS changes take time to propagate across the internet due to caching. If the TTL is set too high, old records may be cached for an extended period, leading to email delivery issues.
Question 4:
Which of the following is required for hosts to receive DHCP addresses from a server that is located on a different subnet?
A. DHCP scope
B. DHCP snooping
C. DHCP reservations
D. DHCP relay
Correct Answer: D
A DHCP relay is a network device that forwards DHCP requests from clients on one subnet to a DHCP server on another subnet. This allows the DHCP server to assign IP addresses and other network configuration parameters to clients across different subnets. A DHCP scope is a range of IP addresses that a DHCP server can assign to clients. A DHCP snooping is a security feature that filters and validates DHCP messages on a switch. A DHCP reservation is a way to assign a specific IP address to a specific client based on its MAC address.
References: Part 2 of the current page talks about DHCP relay and its functions. You can also find more information about DHCP relay on [this page].
Question 5:
A systems administrator is investigating why users cannot reach a Linux web server with a browser but can ping the server IP. The server is online, the web server process is running, and the link to the switch is up. Which of the following commands should the administrator run on the server first?
A. traceroute
B. netstat
C. tcpdump
D. arp
Correct Answer: B
The netstat command provides information about network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. Running netstat on the server can help the administrator verify that the web server process is listening on the expected port (e.g., port 80 for HTTP or port 443 for HTTPS) and that there are no issues with network connections. This is a crucial first step in diagnosing why the web server is not accessible via a browser.
References: CompTIA Network+ study materials.
Question 6:
Which of the following cloud components can filter inbound and outbound traffic between cloud resources?
A. NAT gateways
B. Service endpoints
C. Network security groups
D. Virtual private cloud
Correct Answer: C
Network security groups are cloud components that can filter inbound and outbound traffic between cloud resources based on rules and priorities. Network security groups can be applied to virtual machines, subnets, or network interfaces to control the network access and security. Network security groups can allow or deny traffic based on the source, destination, port, and protocol of the packets. Network security groups are different from NAT gateways, service endpoints, and virtual private clouds, which are other cloud components that have different functions and purposes.
Question 7:
An administrator is configuring a switch that will be placed in an area of the office that is accessible to customers. Which of the following is the best way for the administrator to mitigate unknown devices from connecting to the network?
A. SSE
B. ACL
C. Perimeter network
D. 802.1x
Correct Answer: D
802.1x is a network access control protocol that provides an authentication mechanism to devices trying to connect to a LAN or WLAN. This ensures that only authorized devices can access the network, making it ideal for mitigating the risk of
unknown devices connecting to the network, especially in accessible areas. 802.1x Authentication: Requires devices to authenticate using credentials (e.g., username and password, certificates) before gaining network access. Access
Control: Prevents unauthorized devices from connecting to the network, enhancing security in public or semi-public areas. Implementation: Typically used in conjunction with a RADIUS server to manage authentication requests.
Network References:
CompTIA Network+ N10-007 Official Certification Guide: Covers 802.1x and its role in network security.
Cisco Networking Academy: Provides training on implementing 802.1x for secure network access control.
Network+ Certification All-in-One uide: Explains the benefits and configuration of 802.1x authentication in securing network access.
Question 8:
Before using a guest network, an administrator requires users to accept the terms of use
Which of the following is the best way to accomplish this goal?
A. Pre-shared key
B. Autonomous access point
C. Captive portal
D. WPA2 encryption
Correct Answer: C
A captive portal is a web page that users must view and interact with before being granted access to a network. It is commonly used in guest networks to enforce terms of use agreements. When a user connects to the network, they are redirected to this portal where they must accept the terms of use before proceeding. This method ensures that users are aware of and agree to the network\’s policies, making it the best choice for this scenario.
References: CompTIA Network
+ Exam Objectives and official study guides.
Question 9:
Which of the following authentication methods requires a user to enter a password and scan a fingerprint?
A. Single sign-on
B. Kerberos
C. Multifactor
D. Network access control
Correct Answer: C
Multifactor authentication is a method of verifying a user\’s identity by requiring more than one factor, such as something the user knows, something the user has, or something the user is. A password is something the user knows, and a fingerprint is something the user is.
Therefore, a user who needs to enter a password and scan a fingerprint is using multifactor authentication.
Question 10:
Which of the following is a cost-effective advantage of a split-tunnel VPN?
A. Web traffic is filtered through a web filter.
B. More bandwidth is required on the company\’s internet connection.
C. Monitoring detects insecure machines on the company\’s network.
D. Cloud-based traffic flows outside of the company\’s network.
Correct Answer: D
A split-tunnel VPN allows certain traffic (e.g., cloud-based services) to bypass the VPN and go directly to the Internet. This reduces the amount of traffic that needs to traverse the company\’s VPN and Internet connection, conserving bandwidth and reducing costs. It also means that not all traffic is subject to the same level of inspection or filtering, which can improve performance for cloud-based services.
References: CompTIA Network+ study materials.
Question 11:
A network engineer performed a migration to a new mail server. The engineer changed the MX record, verified the change was accurate, and confirmed the new mail server was reachable via the IP address in the A record. However, users are not receiving email.
Which of the following should the engineer have done to prevent the issue from occurring?
A. Change the email client configuration to match the MX record.
B. Reduce the TTL record prior to the MX record change.
C. Perform a DNS zone transfer prior to the MX record change.
D. Update the NS record to reflect the IP address change.
Correct Answer: B
Understanding TTL (Time to Live):
uk.co.certification.simulator.questionpool.PList@5e5842cf Impact of TTL on DNS Changes:
Best Practice Before Making DNS Changes:
Verification of DNS Changes:
Comparison with Other Options:
References:
CompTIA Network+ study materials and DNS best practices.
Question 12:
A company realizes that only half of its employees work in the office, and the employees who work from home no longer need a computer at the office. Which of the following security measures should the network administrator implement when removing a computer from a cubicle?
A. Disable DHCP on the computer being removed.
B. Place the switch port in a private VLAN.
C. Apply a firewall rule to block the computer\’s IP address.
D. Remove the employee\’s network access.
Correct Answer: D
References
1: CompTIA Network+ N10-008 Cert Guide – O\’Reilly Media
2: Network+ (Plus) Certification | CompTIA IT Certifications
3: 10 Ways to Secure Office Workstations – Computer Security
Question 13:
A network administrator is configuring a wireless network with an ESSID. Which of the following is a user benefit of ESSID compared to SSID?
A. Stronger wireless connection
B. Roaming between access points
C. Advanced security
D. Increased throughput
Correct Answer: B
An Extended Service Set Identifier (ESSID) allows multiple access points to share the same SSID, enabling seamless roaming for users. This means that users can move between different access points within the same ESSID without losing connection or having to reauthenticate. This provides a better user experience, especially in large environments such as office buildings or campuses.
References: CompTIA Network+ study materials.
Question 14:
The cybersecurity department needs to monitor historical IP network traffic on the WAN interface of the outside router without installing network sensors. Which of the following would be best to allow the department to complete this task?
A. Enabling NetFlow on the interface
B. Enabling SSH on the interface
C. Enabling SNMP on the interface
D. Enabling 802.1Q on the interface
Correct Answer: A
Question 15:
SIMULATION
You are tasked with verifying the following requirements are met in order to ensure network security.
Requirements:
Datacenter
– Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
– Provide a dedicated server to resolve IP addresses and hostnames correctly and handle port 53 traffic Building A
–
Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
–
Provide devices to support 5 additional different office users
-Add an additional mobile user
-Replace the Telnet server with a more secure solution Screened subnet
– Ensure network is subnetted to allow all devices to communicate properly while minimizing address space usage
–
Provide a server to handle external 80/443 traffic
–
Provide a server to handle port 20/21 traffic
INSTRUCTIONS
Drag and drop objects onto the appropriate locations. Objects can be used multiple times and not all placeholders need to be filled.
Available objects are located in both the Servers and Devices tabs of the Drag and Drop menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
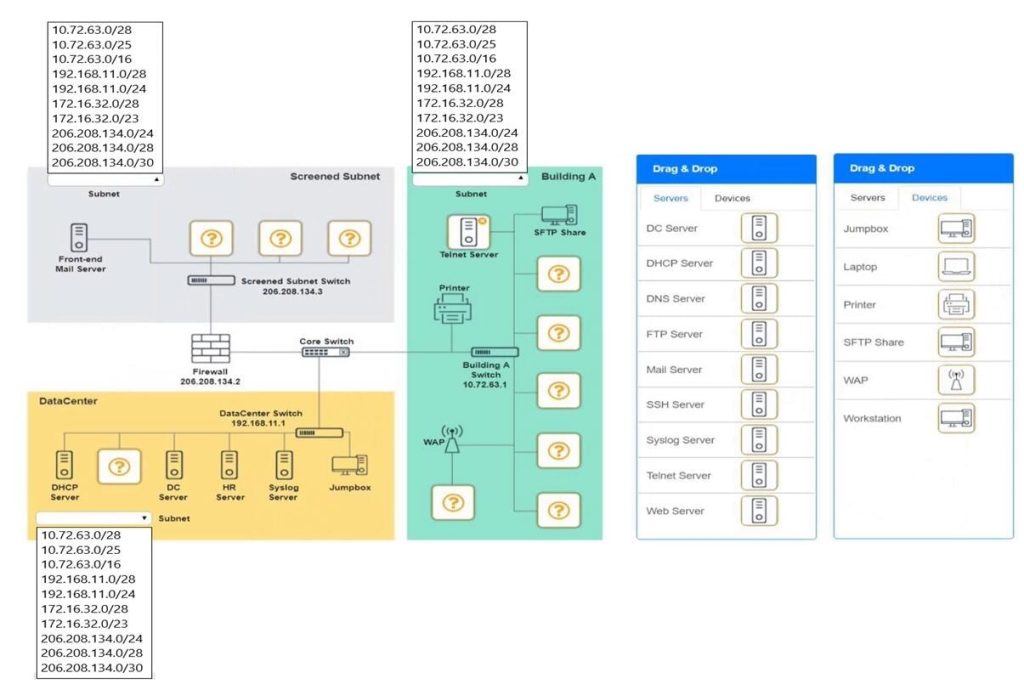
A. See explanation below.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
Top left subnet – 206.208.134.0/28 Top right subnet – 10.72.63.0/28 Bottom subnet – 192.168.11.0/28
Screened Subnet devices – Web server, FTP server Building A devices – SSH server top left, workstations on all 5 on the right, laptop on bottom left DataCenter devices – DNS server.
…
Download the complete CompTIA N10-009 exam questions
Pass4itsure N10-009 dumps contains 263 latest exam questions and answers. It provides two learning tools, VCE and PDF, to help candidates study efficiently and pass the exam. Get 263 latest N10-009 exam questions and answers: https://www.pass4itsure.com/n10-009.html, guaranteed to pass on the first try.