Downloadzpdf update today: Updated CompTIA Security+ SY0-601 exam dumps questions with correct answers as well as parsing! The purpose is to help you quickly pass the CompTIA Security+ 2021 exam. CompTIA SY0-601 is designed to monitor your CompTIA Security+ knowledge, and if you are qualified, you can obtain CompTIA Security+ certification, and the workplace is even more advanced.
Latest version of CompTIA Security+ SY0-601 exam dumps PDF and VCE: https://www.pass4itsure.com/sy0-601.html Come collect valid SY0-601 questions and answers and pass the exam fast!
CompTIA Security+ exam dumps update [2022] real SY0-601 exam materials

Pass4itSure updated SY0-601 dumps free practice exam help you pass the exam.
Verified SY0-601 pdf questions and answers
[google drive] free SY0-601 exam dumps pdf https://drive.google.com/file/d/13fbJWydQz7282l99-FP-FPeKiPTVJlRU/view?usp=sharing
CompTIA Security+ 2021 SY0-601 simulation questions
1. A network administrator would like to configure a site-to-site VPN utilizing iPSec. The administrator wants the tunnel to be established with data integrity encryption, authentication and anti- replay functions Which of the following should the administrator use when configuring the VPN?
A. AH
B. EDR
C. ESP
D. DNSSEC
https://www.hypr.com/encapsulating-security-payload-esp/
Encapsulating Security Payload (ESP) is a member of the Internet Protocol Security (IPsec) set of protocols that encrypt and authenticate the packets of data between computers using a Virtual Private Network (VPN).
The focus and layer on which ESP operates makes it possible for VPNs to function securely.
2. A company is setting up a web server on the Internet that will utilize both encrypted and unencrypted web-browsing protocols. A security engineer runs a port scan against the server from the Internet and sees the following output:
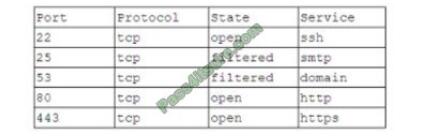
Which of the following steps would be best for the security engineer to take NEXT?
A. Allow DNS access from the internet.
B. Block SMTP access from the Internet
C. Block HTTPS access from the Internet
D. Block SSH access from the Internet.
3. An organization wants to implement a third factor to an existing multifactor authentication. The organization already uses a smart card and password. Which of the following would meet the organization\’s needs for a third factor?
A. Date of birth
B. Fingerprints
C. PIN
D. TPM
4. A university is opening a facility in a location where there is an elevated risk of theft The university wants to protect the desktops in its classrooms and labs Which of the following should the university use to BEST protect these assets deployed in the facility?
A. Visitor logs
B. Cable locks
C. Guards
D. Disk encryption
E. Motion detection
5. A security engineer has enabled two-factor authentication on all workstations. Which of the following approaches are the MOST secure? (Select TWO).
A. Password and security question
B. Password and CAPTCHA
C. Password and smart card
D. Password and fingerprint
E. Password and one-time token
F. Password and voice
6. Which of the following BEST explains the reason why a server administrator would place a document named password.txt on the desktop of an administrator account on a server?
A. The document is a honeyfile and is meant to attract the attention of a cyberintruder.
B. The document is a backup file if the system needs to be recovered.
C. The document is a standard file that the OS needs to verify the login credentials.
D. The document is a keylogger that stores all keystrokes should the account be compromised.
7. A security an alyst needs to implement security features across smartphones. laptops, and tablets
Which of the following would be the MOST effective across heterogeneous platforms?
A. Enforcing encryption
B. Deploying GPOs
C. Removing administrative permissions
D. Applying MDM software
8. A security analyst is reviewing information regarding recent vulnerabilities. Which of the following will the analyst MOST likely consult to validate which platforms have been affected?
A. OSINT
B. SIEM
C. CVSS
D. CVE
CVE entries are brief. They don\\’t include technical data, or information about risks, impacts, and fixes. Those details appear in other databases, including the U.S. National Vulnerability Database (NVD), the CERT/CC Vulnerability Notes Database, and various lists maintained by vendors and other organizations. Across these different systems, CVE IDs give users a reliable way to tell one unique security flaw from another.
9. A security analyst is reviewing a new website that will soon be made publicly available. The analyst sees the following in the URL: http://dev-site.comptia.org/home/show.php?sessionID=77276554andloc=us
The analyst then sends an internal user a link to the new website for testing purposes, and when the user clicks the link, the analyst is able to browse the website with the following URL: http://dev-site.comptia.org/home/show.php?sessionID=98988475andloc=us
Which of the following application attacks is being tested?
A. Pass-the-hash
B. Session replay
C. Object deference
D. Cross-site request forgery
10. A security analyst is Investigating a malware incident at a company. The malware Is accessing a command-and-control website at www.comptia.com. All outbound Internet traffic is logged to a syslog server and stored in /logfiles/messages.
Which of the following commands would be BEST for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?

A. Option A
B. Option B
C. Option C
D. Option D
11. A security analyst discovers several .jpg photos from a cellular phone during a forensics investigation involving a compromised system. The analyst runs a forensics tool to gather file metadata. Which of the following would be part of the images if all the metadata is still intact?
A. The GPS location
B. When the file was deleted
C. The total number of print jobs
D. The number of copies made
12. Which of the following describes the BEST approach for deploying application patches?
A. Apply the patches to systems in a testing environment then to systems in a staging environment, and finally to production systems.
B. Test the patches in a staging environment, develop against them in the development environment, and then apply them to the production systems
C. Test the patches m a test environment apply them to the production systems and then apply them to a staging environment
D. Apply the patches to the production systems apply them in a staging environment, and then test all of them in a testing environment
Correct answer:
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| C | D | B | B | CD | A | D | D | B | C | A | A |
…..
Past CompTIA SY0-601 exam free practice questions:
[2022.1] https://www.downloadzpdf.com/new-comptia-sy0-601-study-guide-actual-exam-questions/
Remember, real SY0-601 exam dumps materials can help you pass the exam quickly.
Pass4itSure SY0-601 exam dumps have been updated https://www.pass4itsure.com/sy0-601.html meet the requirements, practice carefully, and pass exam go once.