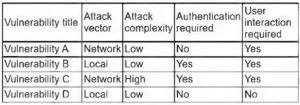
The latest CompTIA SY0-601 exam questions can help you pass the exam! All questions are corrected
to ensure authenticity and effectiveness! Download the Pass4itsure CompTIA SY0-601 dumps https://www.pass4itsure.com/sy0-601.html (Q&As: 298).
[Latest PDF] Free CompTIA SY0-601 pdf dumps download from Google Drive: https://drive.google.com/file/d/1UdzJY4BLJcownN9Xu-E7QLaH9Sh_TOBi/view?usp=sharing
Share CompTIA SY0-601 practice test for free
QUESTION 1
An attacker is attempting to exploit users by creating a fake website with URL users. Which of the following socialengineering attacks does this describe?
A. Information elicitation
B. Typo squatting
C. Impersonation
D. Watering-hole attack
Correct Answer: D
QUESTION 2
A company has decided to move its operations to the cloud. It wants to utilize technology that will prevent users from
downloading company applications for personal use, restrict data that is uploaded, and have visibility into which
applications are being used across the company. Which of the following solutions will BEST meet these requirements?
A. An NGFW
B. A CASB
C. Application whitelisting
D. An NG-SWG
Correct Answer: B
QUESTION 3
A software developer needs to perform code-execution testing, black-box testing, and non- functional testing on a new
product before its general release. Which of the following BEST describes the tasks the developer is conducting?
A. Verification
B. Validation
C. Normalization
D. Staging
Correct Answer: A
QUESTION 4
A technician needs to prevent data loss in a laboratory. The laboratory is not connected to any external networks. Which
of the following methods would BEST prevent the exfiltration of data? (Select TWO).
A. VPN
B. Drive encryption
C. Network firewall
D. File-level encryption
E. USB blocker
F. MFA
Correct Answer: BE
QUESTION 5
An organization\\’s help desk is flooded with phone calls from users stating they can no longer access certain websites.
The help desk escalates the issue to the security team, as these websites were accessible the previous day. The
security analysts run the following command: ipconfig /flushdns, but the issue persists. Finally, an analyst changes the
DNS server for an impacted machine and the issue goes away. Which of the following attacks MOST likely occurred on
the original DNS server?
A. DNS cache poisoning
B. Domain hijacking
C. Distributed denial-of-service
D. DNS tunneling
Correct Answer: B
QUESTION 6
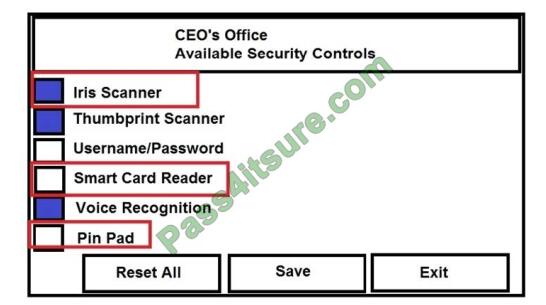
You have just received some room and WiFi access control recommendations from a security consulting company.
Click on each building to bring up available security controls. Please implement the following requirements:
The Chief Executive Officer\\’s (CEO) office had multiple redundant security measures installed on the door to the office.
Remove unnecessary redundancies to deploy three-factor authentication, while retaining the expensive iris render.
The Public Cafe has wireless available to customers. You need to secure the WAP with WPA and place a passphrase
on the customer receipts.
In the Data Center, you need to include the authentication from the “something you know” category and take advantage of
the existing smartcard reader on the door.
In the Help Desk Office, you need to require single factor authentication through the use of physical tokens given to
guests by the receptionist.
The PII Office has redundant security measures in place. You need to eliminate the redundancy while maintaining three-factor authentication and retaining the more expensive controls.
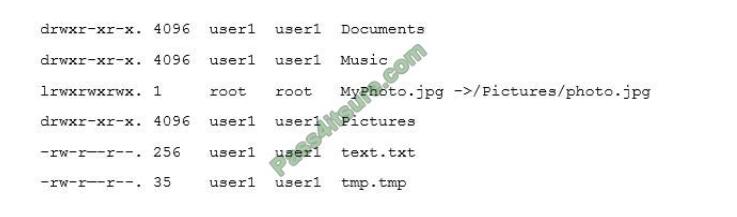
Instructions: The original security controls for each office can be reset at any time by selecting the Reset button. Once
you have met the above requirements for each office, select the Save button. When you have completed the entire
simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to
continue.
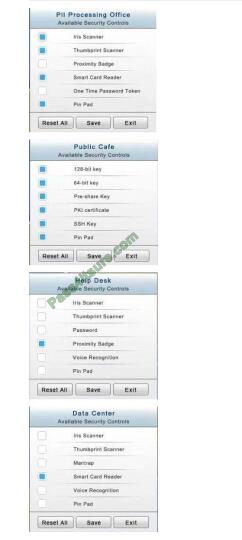

Correct Answer:
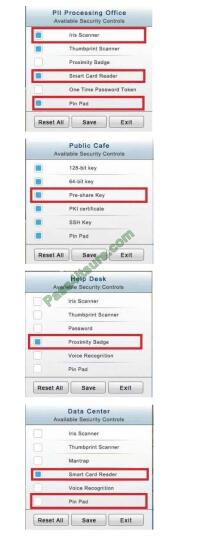
See the solution below.
QUESTION 7
Which of the following types of controls is a turnstile?
A. Physical
B. Detective
C. Corrective
D. Technical
Correct Answer: A
QUESTION 8
Which of the following is MOST likely to outline the roles and responsibilities of data controllers and data processors?
A. SSAE SOC 2
B. PCI DSS
C. GDPR
D. ISO 31000
Correct Answer: C
QUESTION 9
A security analyst is reviewing logs on a server and observes the following output: Which of the following is the security
analyst observing?

A. A rainbow table attack
B. A password-spraying attack
C. A dictionary attack
D. A keylogger attack
Correct Answer: C
QUESTION 10
The SOC is reviewing processes and procedures after a recent incident. The review indicates it took more than 30 minutes
to determine that quarantining an infected host was the best course of action. The allowed the malware to spread to
additional hosts before it was contained. Which of the following would be BEST to improve the incident response
process?
A. Updating the playbooks with better decision points
B. Dividing the network into trusted and untrusted zones
C. Providing additional end-user training on acceptable use
D. Implementing manual quarantining of infected hosts
Correct Answer: A
QUESTION 11
A company recently experienced an attack in which a malicious actor was able to exfiltrate data by cracking stolen
passwords, using a rainbow table the sensitive data. Which of the following should a security engineer do to prevent
such an attack in the future?
A. Use password hashing.
B. Enforce password complexity.
C. Implement password salting.
D. Disable password reuse.
Correct Answer: D
QUESTION 12
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a
routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output:

Which of the following is the router experiencing?
A. DDoS attack
B. Memory leak
C. Buffer overflow
D. Resource exhaustion
Correct Answer: D
QUESTION 13
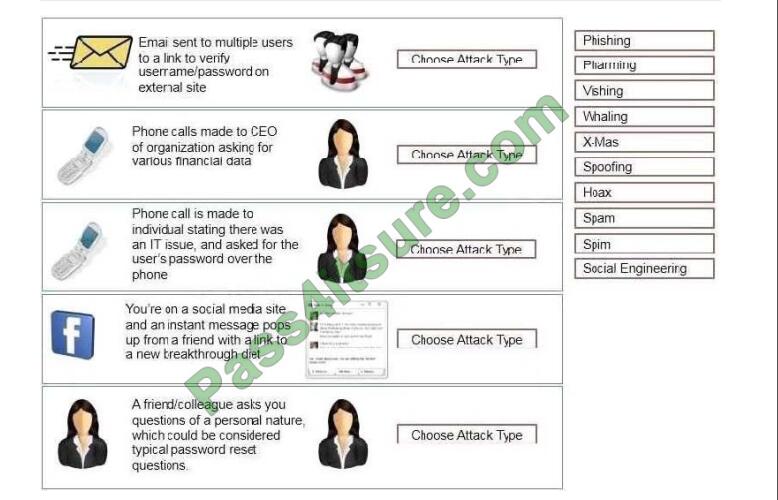
Determine the types of attacks below by selecting an option from the dropdown list. Determine the types of Attacks from
right to a specific action.
Select and Place:
Correct Answer: 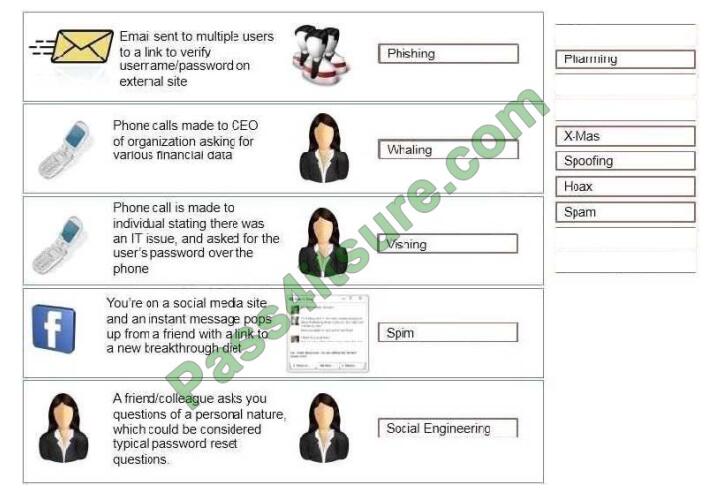
A. Phishing.
B. Whaling.
C. Vishing.
D. Spim.
E. Social engineering.
A: Phishing is the act of sending an email to a user falsely claiming to be an established legitimate enterprise in an
attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing email will direct the user to visit a website where they are asked to update personal information, such as a
password, credit card, social security, or bank account numbers, that the legitimate organization already has. The
website, however, is bogus and set up only to steal the information the user enters on the page.
B: Whaling is a specific kind of malicious hacking within the more general category of phishing, which involves hunting
for data that can be used by the hacker. In general, phishing efforts are focused on collecting personal data about users.
In
whaling, the targets are high-ranking bankers, executives, or others in powerful positions or job titles.
Hackers who engage in whaling often describe these efforts as “reeling in a big fish,” applying a familiar metaphor to the
process of scouring technologies for loopholes and opportunities for data theft. Those who are engaged in whaling
may,
for example, hack into specific networks where these powerful individuals work or store sensitive data. They may also
set up keylogging or other malware on a workstation associated with one of these executives. There are many ways
that
hackers can pursue whaling, leading C-level or top-level executives in business and government to stay vigilant about
the possibility of cyber threats.
C: Vishing is the act of using the telephone in an attempt to scam the user into surrendering private information that will
be used for identity theft. The scammer usually pretends to be a legitimate business, and fools the victim into thinking
he
or she will profit.
D: SPIM is a term sometimes used to refer to spam over IM (Instant Messaging). It\\’s also called just spam, instant
spam, or IM marketing. No matter what the name, it consists of unwanted messages transmitted through some form of
instant
messaging service, which can include Short Message Service (SMS).
E: Social engineering is a non-technical method of intrusion hackers use that relies heavily on human interaction and
often involves tricking people into breaking normal security procedures. It is one of the greatest threats that
organizations
today encounter.
A social engineer runs what used to be called a “con game.” For example, a person using social engineering to break
into a computer network might try to gain the confidence of an authorized user and get them to reveal information that
compromises the network\\’s security. Social engineers often rely on the natural helpfulness of people as well as on their
weaknesses. They might, for example, call the authorized employee with some kind of urgent problem that requires
immediate network access. Appealing to vanity, appealing to authority, appealing to greed, and old-fashioned
eavesdropping is another typical social engineering technique.
References:
http://www.webopedia.com/TERM/P/phishing.html
http://www.techopedia.com/definition/28643/whaling
http://www.webopedia.com/TERM/V/vishing.html
http://searchsecurity.techtarget.com/definition/social-engineering
Latest CompTIA SY0-601 google drive
CompTIA SY0-601 pdf https://drive.google.com/file/d/1UdzJY4BLJcownN9Xu-E7QLaH9Sh_TOBi/view?usp=sharing
Summarize:
This blog shares the latest CompTIA SY0-601 exam questions, and answers! CompTIA SY0-601 pdf!
You can also practice the test online! Pass4itsure is the industry leader! Go https://www.pass4itsure.com/sy0-601.html Help you successfully pass the CompTIA SY0-601 exam.
ps.
Free CompTIA SY0-601 dumps pdf download: https://drive.google.com/file/d/1UdzJY4BLJcownN9Xu-E7QLaH9Sh_TOBi/view?usp=sharing