The great Pass4itSure refreshed the CompTIA CS0-002 dumps pdf in April, so keep practicing the real exam practice and improve your CompTIA Cybersecurity Analyst (CySA+) exam to pass the CompTIA CySA+ exam in one go.
Just buy the full CompTIA CS0-002 dumps pdf: https://www.pass4itsure.com/cs0-002.html
Don’t know where to practice? Practice on the free CompTIA CS0-002 practice test provided by Pass4itSure and get free CS0-002 dumps with verified answers and detailed explanations!
The free CompTIA CS0-002 practice test questions are as follows:
01. When investigating a compromised system, a security analyst finds the following script in the /tmp directory: PASS=password123 for user in \\’ cat allusers.txt\\’ do ./trylogin.py dc1.comptia.org $user $PASS done Which of the following attacks is this script attempting, and how can it be mitigated?
A. This is a password-hijacking attack, and it can be mitigated by using strong encryption protocols.
B. This is a password-spraying attack, and it can be mitigated by using multifactor authentication.
C. This is a password-dictionary attack, and it can be mitigated by forcing password changes every 30 days.
D. This is a credential-stuffing attack, and it can be mitigated by using multistep authentication.
02. As part of an organization\\’s information security governance process, a Chief Information Security Officer (CISO) is working with the compliance officer to update policies to include statements related to new regulatory and legal requirements. Which of the following should be done to BEST ensure all employees are appropriately aware of changes to the policies?
A. Conduct a risk assessment based on the controls defined in the newly revised policies
B. Require all employees to attend updated security awareness training and sign an acknowledgment
C. Post the policies on the organization\\’s intranet and provide copies of any revised policies to all active vendors
D. Distribute revised copies of policies to employees and obtain a signed acknowledgment from them
03. A security analyst has determined that the user interface on an embedded device is vulnerable to common SQL injections. The device is unable to be replaced, and the software cannot be upgraded. Which of the following should the security analyst recommend to add additional security to this device?
A. The security analyst should recommend this device be placed behind a WAF.
B. The security analyst should recommend an IDS be placed on the network segment.
C. The security analyst should recommend this device regularly export the weblogs to a SIEM system.
D. The security analyst should recommend this device be included in regular vulnerability scans.
04. A software patch has been released to remove vulnerabilities from the company\\’s software. A security analyst has been tasked with testing the software to ensure the vulnerabilities have been remediated and the application is still functioning properly. Which of the following tests should be performed NEXT?
A. Fuzzing
B. User acceptance testing
C. Regression testing
D. Penetration testing
Reference: https://en.wikipedia.org/wiki/Regression_testing
05. A manufacturing company has decided to participate in direct sales of its products to consumers. The company decides to use a subdomain of its main site with its existing cloud service provider as the portal for e-commerce. After launch, the site is stable and functions properly, but after a robust day of sales, the site begins to redirect to a competitor\\’s landing page.
Which of the following actions should the company\\’s security team take to determine the cause of the issue and minimize the scope of impact?
A. Engage a third party to provide penetration testing services to see if an exploit can be found
B. Check DNS records to ensure Cname or alias records are in place for the subdomain
C. Query, the cloud provider to determine the nature of the DNS attack and find out which other clients are affected
D. Check the DNS records to ensure a correct MX record is established for the subdomain
06. An analyst is reviewing the following log from the company web server:

Which of the following is this an example of?
A. Online rainbow table attack
B. Offline brute force attack
C. Offline dictionary attack
D. Online hybrid attack
07. A security architect is reviewing the options for performing input validation on incoming web form submissions. Which of the following should the architect as the MOST secure and manageable option?
A. Client-side whitelisting
B. Server-side whitelisting
C. Server-side blacklisting
D. Client-side blacklisting
08. A cybersecurity analyst is reading a daily intelligence digest of new vulnerabilities The type of vulnerability that should be disseminated FIRST is one that:
A. enables remote code execution that is being exploited in the wild.
B. enables data leakage but is not known to be m the environment
C. enables lateral movement and was reported as a proof of concept
D. affected the organization in the past but was probably contained and eradicated
09. Which of the following organizations would have to remediate embedded controller vulnerabilities?
A. Banking institutions
B. Public universities
C. Regulatory agencies
D. Hydroelectric facilities
10. A technician receives the following security alert from the firewall\\’s automated system:
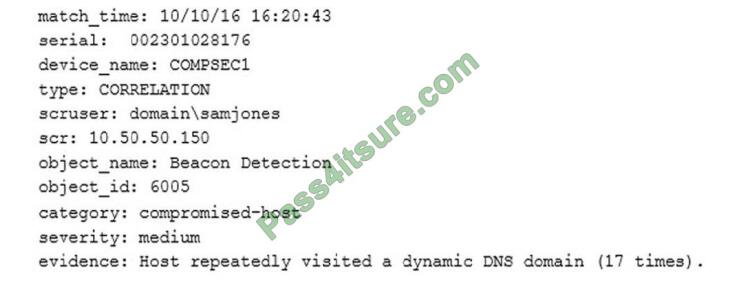
After reviewing the alert, which of the following is the BEST analysis?
A. This alert is a false positive because DNS is a normal network function.
B. This alert indicates a user was attempting to bypass security measures using dynamic DNS.
C. This alert was generated by the SIEM because the user attempted too many invalid login attempts.
D. This alert indicates an endpoint may be infected and is potentially contacting a suspect host.
11. A corporation has implemented an 802.1X wireless network using self-signed certificates. Which of the following represents a risk to wireless users?
A. Buffer overflow attacks
B. Cross-site scripting attacks
C. Man-in-the-middle attacks
D. Denial of service attacks
12. An organization needs to limit its exposure to accidental disclosure when employees send emails that contain personal information to recipients outside the company Which of the following technical controls would BEST accomplish this goal?
A. DLP
B. Encryption
C. Data masking
D. SPF
13. During an incident investigation, a security analyst acquired a malicious file that was used as a backdoor but was not detected by the antivirus application. After performing a reverse-engineering procedure, the analyst found that part of the code was obfuscated to avoid signature detection.
Which of the following types of instructions should the analyst use to understand how the malware was obfuscated and to help deobfuscate it?
A. MOV
B. ADD
C. XOR
D. SUB
E. MOVL
Answer:
| 01 | 02 | 03 | 04 | 05 | 06 | 07 | 08 | 09 | 10 | 11 | 12 | 13 |
| D | B | A | C | B | B | B | C | D | D | C | C | C |
Also for you, a free CompTIA CS0-002 dumps pdf download:
google drive: https://drive.google.com/file/d/11Haexh51oF23vhBkDE1eBHFaW45wyUKg/view?usp=sharing
Get the latest CompTIA CS0-002 dumps pdf https://www.pass4itsure.com/cs0-002.html and pass the exam on your first attempt.