The latest CompTIA CAS-003 exam questions can help you pass the exam! All questions are corrected
to ensure authenticity and effectiveness! Download the Pass4itsure CompTIA CAS-003 dumps https://www.pass4itsure.com/cas-003.html (Q&As: 682).
[Latest PDF] Free CompTIA CAS-003 pdf dumps download from Google Drive: https://drive.google.com/file/d/1Js2RqN0E0ydUQN8_mv_otRmegZW6YLGB/view?usp=sharing
Share CompTIA CAS-003 practice test for free
QUESTION 1
A security consultant was hired to audit a company\\’s password are account policy. The company implements the
following controls:
1.
Minimum password length: 16
2.
Maximum password age: 0
3.
Minimum password age: 0
4.
Password complexity: disabled
5.
Store passwords in plain text: disabled
6.
Failed attempts lockout: 3
7.
Lockout timeout: 1 hour
The password database uses salted hashes and PBKDF2. Which of the following is MOST likely to yield the greatest
number of plain text passwords in the shortest amount of time?
A. Offline hybrid dictionary attack
B. Offline brute-force attack
C. Online hybrid dictionary password spraying attack
D. Rainbow table attack
E. Online brute-force attack
F. Pass-the-hash attack
Correct Answer: C
QUESTION 2
A security administrator wants to implement controls to harden company-owned mobile devices. Company policy specifies the following requirements:
1.
Mandatory access control must be enforced by the OS.
2.
Devices must only use the mobile carrier data transport.
Which of the following controls should the security administrator implement? (Select three).
A. Enable DLP
B. Enable SEAndroid
C. Enable EDR
D. Enable secure boot
E. Enable remote wipe
F. Disable Bluetooth
G. Disable 802.11
H. Disable geotagging
Correct Answer: BFG
QUESTION 3
Following a recent and very large corporate merger, the number of log files an SOC needs to review has approximately
tripled. The Chief Information Security Officer (CISO) has not been allowed to hire any more staff for the SOC, but is
looking for other ways to automate the log review process so the SOC receives less noise. Which of the following would
BEST reduce log noise for the SOC?
A. SIEM filtering
B. Machine learning
C. Outsourcing
D. Centralized IPS
Correct Answer: A
QUESTION 4
A security administrator is advocating for enforcement of a new policy that would require employers with privileged
access accounts to undergo periodic inspections and review of certain job performance data. To which of the following
policies is the security administrator MOST likely referring?
A. Background investigation
B. Mandatory vacation
C. Least privilege
D. Separation of duties
Correct Answer: C
QUESTION 5
An external red team member conducts a penetration test, attempting to gain physical access to a large organization\\’s
server room in a branch office. During reconnaissance, the red team member sees a clearly marked door to the server
room, located next to the lobby, with a tumbler lock.
Which of the following is BEST for the red team member to bring on site to open the locked door as quickly as possible
without causing significant damage?
A. Screwdriver set
B. Bump key
C. RFID duplicator
D. Rake picking
Correct Answer: D
QUESTION 6
A security engineer is working on a large software development project. As part of the design of the
project, various stakeholder requirements were gathered and decomposed to an implementable and
testable level.
Various security requirements were also documented.
Organize the following security requirements into the correct hierarchy required for an SRTM.
Requirement 1: The system shall provide confidentiality for data in transit and data at rest.
Requirement 2: The system shall use SSL, SSH, or SCP for all data transport.
Requirement 3: The system shall implement a file-level encryption scheme.
Requirement 4: The system shall provide integrity for all data at rest.
Requirement 5: The system shall perform CRC checks on all files.
A. Level 1: Requirements 1 and 4; Level 2: Requirements 2, 3, and 5 B. Level 1: Requirements 1 and 4; Level 2:
Requirements 2 and 3 under 1, Requirement 5 under 4
C. Level 1: Requirements 1 and 4; Level 2: Requirement 2 under 1, Requirement 5 under 4; Level 3: Requirement 3
under 2
D. Level 1: Requirements 1, 2, and 3; Level 2: Requirements 4 and 5
Correct Answer: B
Confidentiality and integrity are two of the key facets of data security. Confidentiality ensures that sensitive information
is not disclosed to unauthorized users; while integrity ensures that data is not altered by unauthorized users. These are
Level 1 requirements.
Confidentiality is enforced through encryption of data at rest, encryption of data in transit, and access control. Encryption
of data in transit is accomplished by using secure protocols such as PSec, SSL, PPTP, SSH, and SCP, etc.
Integrity can be enforced through hashing, digital signatures and CRC checks on the files.
In the SRTM hierarchy, the enforcement methods would fall under the Level requirement.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley and Sons,
Indianapolis, 2012, pp. 17-19, 20, 27-29
QUESTION 7
Joe, a hacker, has discovered he can specifically craft a webpage that when viewed in a browser crashes the browser
and then allows him to gain remote code execution in the context of the victim\\’s privilege level. The browser crashes
due to an exception error when a heap memory that is unused is accessed. Which of the following BEST describes the
application issue?
A. Integer overflow
B. Click-jacking
C. Race condition
D. SQL injection
E. Use after free
F. Input validation
Correct Answer: E
Use-After-Free vulnerabilities are a type of memory corruption flaw that can be leveraged by hackers to execute
arbitrary code.
Use After Free specifically refers to the attempt to access memory after it has been freed, which can cause a program to
crash or, in the case of a Use-After-Free flaw, can potentially result in the execution of arbitrary code or even enable full
remote code execution capabilities.
According to the Use After Free definition on the Common Weakness Enumeration (CWE) website, a Use After Free
scenario can occur when “the memory in question is allocated to another pointer validly at some point after it has been
freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the
data is changed, it corrupts the validly used memory; this induces undefined behavior in the process.”
QUESTION 8
A cybersecurity analyst is conducting packet analysis on the following: Which of the following is occurring in the given
packet capture?
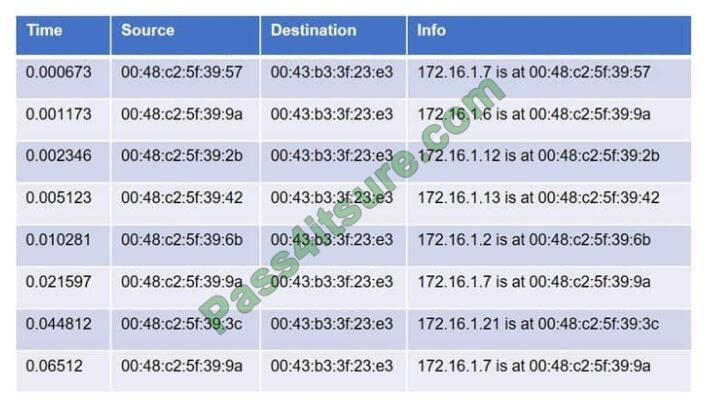
A. ARP spoofing
B. Broadcast storm
C. Smurf attack
D. Network enurneration
E. Zero-day exploit
Correct Answer: A
QUESTION 9
Management is reviewing the results of a recent risk assessment of the organization\\’s policies and procedures. During
the risk assessment it is determined that procedures associated with background checks have not been effectively
implemented. In response to this risk, the organization elects to revise policies and procedures related to background
checks and use a third-party to perform background checks on all new employees.
Which of the following risk management strategies has the organization employed?
A. Transfer
B. Mitigate
C. Accept
D. Avoid
E. Reject
Correct Answer: B
QUESTION 10
A security analyst is reviewing the following packet capture of communication between a host and a company\\’s router:

Which of the following actions should the security analyst take to remove this vulnerability?
A. Update the router code
B. Implement a router ACL
C. Disconnect the host from the network
D. Install the latest antivirus definitions
E. Deploy a network-based IPS
Correct Answer: B
QUESTION 11
A forensic analyst suspects that a buffer overflow exists in a kernel module. The analyst executes the following
command:
dd if=/dev/ram of=/tmp/mem/dmp The analyst then reviews the associated output:
^34^#AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA/bin/bash^21^03#45
However, the analyst is unable to find any evidence of the running shell.
Which of the following of the MOST likely reason the analyst cannot find a process ID for the shell?
A. The NX bit is enabled
B. The system uses ASLR
C. The shell is obfuscated
D. The code uses dynamic libraries
Correct Answer: B
QUESTION 12
A large hospital has implemented BYOD to allow doctors and specialists the ability to access patient medical records on
their tablets. The doctors and specialists access patient records over the hospital\\’s guest WiFi network which is
isolated from the internal network with appropriate security controls. The patient records management system can be
accessed from the guest network and require two factor authentication. Using a remote desktop type interface, the
doctors and specialists can interact with the hospital\\’s system. Cut and paste and printing functions are disabled to
prevent the copying of data to BYOD devices. Which of the following are of MOST concern? (Select TWO).
A. Privacy could be compromised as patient records can be viewed in uncontrolled areas.
B. Device encryption has not been enabled and will result in a greater likelihood of data loss.
C. The guest WiFi may be exploited allowing non-authorized individuals access to confidential patient data.
D. Malware may be on BYOD devices which can extract data via key logging and screen scrapes.
E. Remote wiping of devices should be enabled to ensure any lost device is rendered inoperable.
Correct Answer: AD
Privacy could be compromised because patient records can be from a doctor\\’s personal device. This can then be
shown to persons not authorized to view this information. Similarly, the doctor\\’s personal device could have malware
on it.
QUESTION 13
A security controls assessor intends to perform a holistic configuration compliance test of networked assets. The
assessor has been handed a package of definitions provided in XML format, and many of the files have two common
tags within them: “” and “”. Which of the following tools BEST supports the use of these definitions?
A. HTTP interceptor
B. Static code analyzer
C. SCAP scanner
D. XML fuzzer
Correct Answer: D
Latest CompTIA CAS-003 google drive
CompTIA CAS-003 pdf https://drive.google.com/file/d/1Js2RqN0E0ydUQN8_mv_otRmegZW6YLGB/view?usp=sharing
Summarize:
This blog shares the latest CompTIA CAS-003 exam questions, and answers! CompTIA CAS-003 pdf!
You can also practice the test online! Pass4itsure is the industry leader! Go https://www.pass4itsure.com/cas-003.html Help you successfully pass the CompTIA CAS-003 exam.
ps.
Free CompTIA CAS-003 dumps pdf download: https://drive.google.com/file/d/1Js2RqN0E0ydUQN8_mv_otRmegZW6YLGB/view?usp=sharing