The latest CompTIA CS0-002 exam questions can help you pass the exam! All questions are corrected
to ensure authenticity and effectiveness! Download the Pass4itsure CompTIA CS0-002 dumps https://www.pass4itsure.com/cs0-002.html (Q&As: 196).
[Latest PDF] Free CompTIA CS0-002 pdf dumps download from Google Drive: https://drive.google.com/file/d/1Y0N4Ex3JbiMidF2dW6hbwaesSVsRsnl-/view?usp=sharing
Share CompTIA CS0-002 practice test for free
QUESTION 1
A security analyst gathered forensics from a recent intrusion in preparation for legal proceedings. The analyst used
EnCase to gather the digital forensics, cloned the hard drive, and took the hard drive home for further analysis. Which of
the following did the security analyst violate?
A. Cloning procedures
B. Chain of custody
C. Hashing procedures
D. Virtualization
Correct Answer: B
QUESTION 2
A security team wants to make SaaS solutions accessible from only the corporate campus. Which of the following would
BEST accomplish this goal?
A. Geofencing
B. IP restrictions
C. Reverse proxy
D. Single sign-on
Correct Answer: A
Reference: https://bluedot.io/library/what-is-geofencing/
QUESTION 3
A developer wrote a script to make names and other Pll data unidentifiable before loading a database export into the
testing system Which of the following describes the type of control that is being used?
A. Data encoding
B. Data masking
C. Data loss prevention
D. Data classification
Correct Answer: B
QUESTION 4
A security analyst is reviewing the logs from an internal chat server. The chat.log file is too large to review manually, so
the analyst wants to create a shorter log file that only includes lines associated with a user demonstrating anomalous
activity. Below is a snippet of the log:
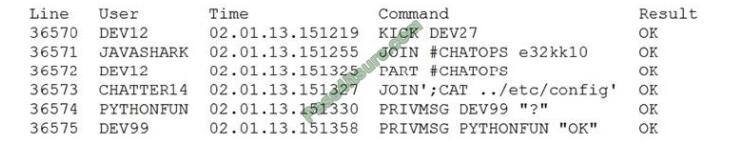
Which of the following commands would work BEST to achieve the desired result?
A. grep -v chatter14 chat.log
B. grep -i pythonfun chat.log
C. grep -i javashark chat.log
D. grep -v javashark chat.log
E. grep -v pythonfun chat.log
F. grep -i chatter14 chat.log
Correct Answer: D
QUESTION 5
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior
results in the industrial generators overheating and destabilizing the power supply. Which of the following would BEST
identify potential indicators of compromise?
A. Use Burp Suite to capture packets to the SCADA device\\’s IP.
B. Use tcpdump to capture packets from the SCADA device IP.
C. Use Wireshark to capture packets between SCADA devices and the management system.
D. Use Nmap to capture packets from the management system to the SCADA devices.
Correct Answer: C
A. enables remote code execution that is being exploited in the wild
B. enables data leakage but is not known to be in the environment
C. enables lateral movement and was reported as a proof of concept
D. affected the organization in the past but was probably contained and eradicated
Correct Answer: A
QUESTION 7
While preparing for an audit of information security controls in the environment, an analyst outlines a framework control
that has the following requirements:
1.
All sensitive data must be classified.
2.
All sensitive data must be purged on a quarterly basis.
3.
Certificates of disposal must remain on file for at least three years.
This framework control is MOST likely classified as:
A. prescriptive
B. risk-based
C. preventive
D. corrective
Correct Answer: A
QUESTION 8
As part of a review of incident response plans, which of the following is MOST important for an organization to
understand when establishing the breach notification period?
A. Organizational policies
B. Vendor requirements and contracts
C. Service-level agreements
D. Legal requirements
Correct Answer: D
QUESTION 9
A network attack that is exploiting a vulnerability in the SNMP is detected. Which of the following should the
cybersecurity analyst do FIRST?
A. Apply the required patches to remediate the vulnerability.
B. Escalate the incident to senior management for guidance.
C. Disable all privileged user accounts on the network.
D. Temporarily block the attacking IP address.
Correct Answer: A
Reference: https://beyondsecurity.com/scan-pentest-network-vulnerabilities-snmp-protocol-version-detection.html
QUESTION 10
During an investigation, an incident responder intends to recover multiple pieces of digital media. Before removing the
media, the responder should initiate:
A. malware scans.
B. secure communications.
C. chain of custody forms.
D. decryption tools.
Correct Answer: C
QUESTION 11
An analyst is participating in the solution analysis process for a cloud-hosted SIEM platform to centralize log monitoring
and alerting capabilities in the SOC. Which of the following is the BEST approach for supply chain assessment when
selecting a vendor?
A. Gather information from providers, including datacenter specifications and copies of audit reports.
B. Identify SLA requirements for monitoring and logging.
C. Consult with senior management for recommendations.
D. Perform a proof of concept to identify possible solutions.
Correct Answer: B
QUESTION 12
Which of the following is the use of tools to simulate the ability for an attacker to gain access to a specified network?
A. Reverse engineering
B. Fuzzing
C. Penetration testing
D. Network mapping
Correct Answer: C
QUESTION 13
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When
conducting the scan, the analyst received the following code snippet of results:
Mail Server1 Trying 192.168.2.2 Connected Get /HTTP/ 1.0
HTTP:1.0 200 Document follows Server: server/0.10 Connection: close Set-Cookie: testing=1; path=/
Which of the following describes the output of this scan?
A. The analyst has discovered a False Positive, and the status code is incorrect providing an OK message.
B. The analyst has discovered a True Positive, and the status code is correct providing a file not found error message.
C. The analyst has discovered a True Positive, and the status code is incorrect providing a forbidden message.
D. The analyst has discovered a False Positive, and the status code is incorrect providing a server error message.
Correct Answer: B
Latest CompTIA CS0-002 google drive
CompTIA CS0-002 pdf https://drive.google.com/file/d/1Y0N4Ex3JbiMidF2dW6hbwaesSVsRsnl-/view?usp=sharing
Summarize:
This blog shares the latest CompTIA CS0-002 exam questions, and answers! CompTIA CS0-002 pdf!
You can also practice the test online! Pass4itsure is the industry leader! Go https://www.pass4itsure.com/cs0-002.html Help you successfully pass the CompTIA CS0-002 exam.
ps.
Free CompTIA CS0-002 dumps pdf download: https://drive.google.com/file/d/1Y0N4Ex3JbiMidF2dW6hbwaesSVsRsnl-/view?usp=sharing