The latest CompTIA SY0-501 exam questions can help you pass the exam! All questions are corrected
to ensure authenticity and effectiveness! Download the Pass4itsure CompTIA SY0-501 dumps https://www.pass4itsure.com/sy0-501.html (Q&As: 1334).
[Latest PDF] Free CompTIA SY0-501 pdf dumps download from Google Drive: https://drive.google.com/file/d/1Ep7Iwiet88u7WghGzlu9sNtBS6kmyzBM/view?usp=sharing
Share CompTIA SY0-501 practice test for free
QUESTION 1
Which of the following BEST describes the concept of perfect forward secrecy?
A. Using quantum random number generation to make decryption effectively impossible
B. Preventing cryptographic reuse so a compromise of one operation does not affect other operations
C. Implementing elliptic curve cryptographic algorithms with true random numbers
D. The use of NDAs and policy controls to prevent disclosure of company secrets
Correct Answer: B
QUESTION 2
A company is performing an analysis of the corporate enterprise network with the intent of identifying any one system,
person, function, or service that, when neutralized, will cause or cascade disproportionate damage to the company\\’s
revenue, referrals, and reputation.
Which of the following an element of the BIA that this action is addressing?
A. Identification of critical systems
B. Single point of failure
C. Value assessment
D. Risk register
Correct Answer: A
QUESTION 3
A Chief Information Security Officer (CISO) asks the security architect to design a method for contractors to access the
company\\’s internal wiki, corporate directory, and email services securely without allowing access to systems beyond
the scope of their project. Which of the following methods would BEST fit the needs of the CISO?
A. VPN
B. PaaS
C. laaS
D. VDI
Correct Answer: A
QUESTION 4
A security administrator is investigating a possible account compromise. The administrator logs onto a desktop
computer, executes the command notepad.exe c:\Temp\qkakforlkgfkja.1og, and reviews the following: Lee,\rI have
completed the task that was assigned to me\rrespectfully\rJohn\r https://www.portal.com\rjohnuser\rilovemycat2 Given
the above output, which of the following is the MOST likely cause of this compromise?
A. Virus
B. Worm
C. Rootkit
D. Keylogger
Correct Answer: D
QUESTION 5
Which of the following characteristics differentiate a rainbow table attack from a brute force attack? (Select two.)
A. Rainbow table attacks greatly reduce compute cycles at attack time.
B. Rainbow tables must include precomputed hashes.
C. Rainbow table attacks do not require access to hashed passwords.
D. Rainbow table attacks must be performed on the network.
E. Rainbow table attacks bypass maximum failed login restrictions.
Correct Answer: BE
QUESTION 6
A vulnerability scanner that uses its running service\\’s access level to better assess vulnerabilities across multiple
assets within an organization is performing a:
A. Credentialed scan.
B. Non-intrusive scan.
C. Privilege escalation test.
D. Passive scan.
Correct Answer: A
QUESTION 7
Which of the following serves to warn users against downloading and installing pirated software on company devices?
A. AUP
B. NDA
C. ISA
D. BPA
Correct Answer: A
QUESTION 8
A network technician needs to monitor and view the websites that are visited by an employee. The employee is
connected to a network switch. Which of the following would allow the technician to monitor the employee\\’s web
traffic?
A. Implement promiscuous mode on the NIC of the employee\\’s computer.
B. Install and configured a transparent proxy server.
C. Run a vulnerability scanner to capture DNS packets on the router.
D. Configure a VPN to forward packets to the technician\\’s computer.
Correct Answer: B
QUESTION 9
A company is terminating an employee for misbehavior. Which of the following steps is MOST important in the process
of disengagement from this employee?
A. Obtain a list of passwords used by the employee.
B. Generate a report on outstanding projects the employee handled.
C. Have the employee surrender company identification.
D. Have the employee sign an NDA before departing.
Correct Answer: C
QUESTION 10
A security analyst monitors the syslog server and notices the following:
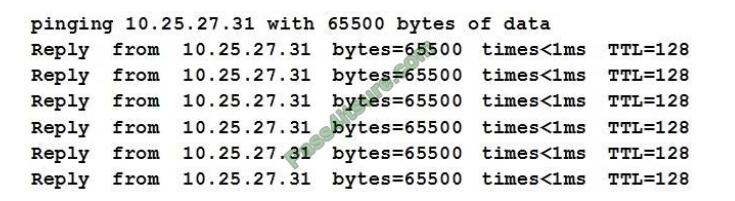
A. Memory leak
B. Buffer overflow
C. Null pointer deference
D. Integer overflow
Correct Answer: B
QUESTION 11
Which of the following would be considered multifactor authentication?
A. Hardware token and smart card
B. Voice recognition and retina scan
C. Strong password and fingerprint
D. PIN and security Question,s
Correct Answer: C
QUESTION 12
A security analyst is inspecting the results of a recent internal vulnerability scan that was performed against intranet
services. The scan reports include the following critical-rated vulnerability:
Title: Remote Command Execution vulnerability in web server Rating: Critical (CVSS 10.0) Threat actor: any remote
user of the web server Confidence: certain Recommendation: apply vendor patches
Which of the following actions should the security analyst perform FIRST?
A. Escalate the issue to senior management.
B. Apply organizational context to the risk rating.
C. Organize for urgent out-of-cycle patching.
D. Exploit the server to check whether it is a false positive.
Correct Answer: B
QUESTION 13
Which of the following strategies helps reduce risk if a rollback is needed when upgrading a critical system platform?
A. Non-persistent configuration
B. Continuous monitoring
C. Firmware updates
D. Fault tolerance
Correct Answer: A
Latest CompTIA SY0-501 google drive
CompTIA SY0-501 pdf https://drive.google.com/file/d/1Ep7Iwiet88u7WghGzlu9sNtBS6kmyzBM/view?usp=sharing
Summarize:
This blog shares the latest CompTIA SY0-501 exam questions, and answers! CompTIA SY0-501 pdf!
You can also practice the test online! Pass4itsure is the industry leader! Go https://www.pass4itsure.com/sy0-501.html Help you successfully pass the CompTIA SY0-501 exam.
ps.
Free CompTIA SY0-501 dumps pdf download: https://drive.google.com/file/d/1Ep7Iwiet88u7WghGzlu9sNtBS6kmyzBM/view?usp=sharing