The latest CompTIA SY0-601 exam questions can help you pass the exam! All questions are corrected
to ensure authenticity and effectiveness! Download the Pass4itsure CompTIA SY0-601 dumps https://www.pass4itsure.com/sy0-601.html (Q&As: 289).
[Latest PDF] Free CompTIA SY0-601 pdf dumps download from Google Drive: https://drive.google.com/file/d/1uN4EuabH-KOdfK7fisemo4B04FPodt5P/view?usp=sharing
Share CompTIA SY0-601 practice test for free
QUESTION 1
Which of the following is the purpose of a risk register?
A. To define the level or risk using probability and likelihood
B. To register the risk with the required regulatory agencies
C. To identify the risk, the risk owner, and the risk measures
D. To formally log the type of risk mitigation strategy the organization is using
Correct Answer: C
QUESTION 2
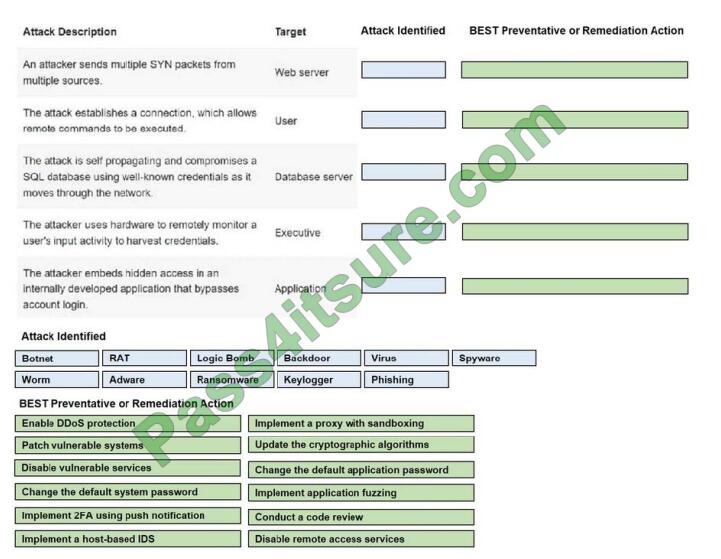
HOTSPOT
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its
remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the
simulation, please click the Reset All button.
Select and Place:
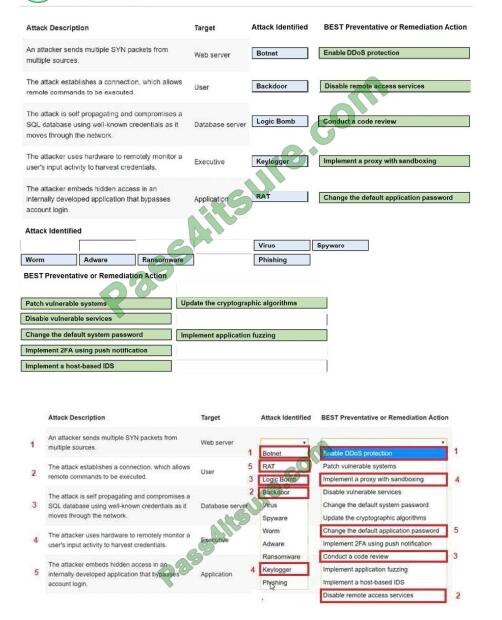
Correct Answer:
QUESTION 3
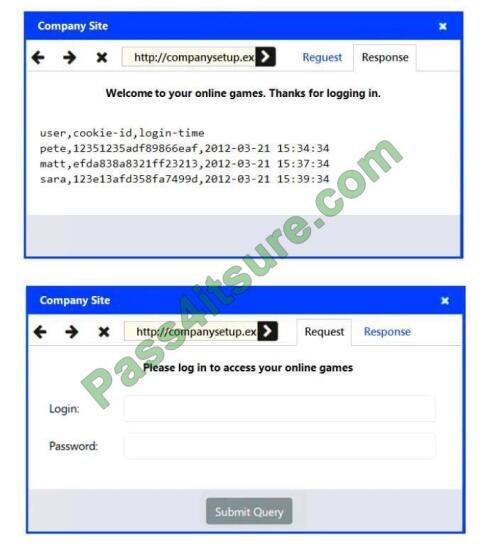
A security analyst has received several reports of an issue on an internal web application. Users state they are having to
provide their credentials twice to log in. The analyst checks with the application team and notes this is not an expected
behavior. After looking at several logs, the analyst decides to run some commands on the gateway and obtains the
following output:
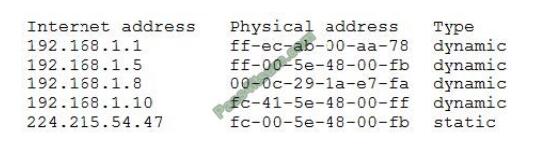
Which of the following BEST describes the attack the company is experiencing?
A. MAC flooding
B. URL redirection
C. ARP poisoning
D. DNS hijacking
Correct Answer: C
ARP Poisoning (also known as ARP Spoofing) is a type of cyber attack carried out over a Local Area Network (LAN)
that involves sending malicious ARP packets to a default gateway on a LAN in order to change the pairings in its IP to
MAC address table. ARP Protocol translates IP addresses into MAC addresses.
QUESTION 4
In which of the following common use cases would steganography be employed?
A. Obfuscation
B. Integrity
C. Non-repudiation
D. Blockchain
Correct Answer: A
QUESTION 5
A user receives a security alert pop-up from the host-based IDS, and a few minutes later notices a document on the
desktop has disappeared and in its place is an odd filename with no icon image. When clicking on this icon, the user
receives a system notification that it cannot find the correct program to use to open this file. Which of the following types
of malware has MOST likely targeted this workstation?
A. Rootkit
B. Spyware
C. Ransomware
D. Remote-access Trojan
Correct Answer: C
QUESTION 6
An organization\\’s help desk is flooded with phone calls from users stating they can no longer access certain websites.
The help desk escalates the issue to the security team, as these websites were accessible the previous day. The
security analysts run the following command: ipconfig /flushdns, but the issue persists. Finally, an analyst changes the
DNS server for an impacted machine, and the issue goes away. Which of the following attacks MOST likely occurred on
the original DNS server?
A. DNS cache poisoning
B. Domain hijacking
C. Distributed denial-of-service
D. DNS tunneling
Correct Answer: B
QUESTION 7
A technician has been asked to document which services are running on each of a collection of 200 servers. Which of
the following tools BEST meets this need while minimizing the work required?
A. Nmap
B. Nslookup
C. Netcat
D. Netstat
Correct Answer: D
QUESTION 8
A startup company is using multiple SaaS and laaS platforms to stand up a corporate infrastructure and build out a
customer-facing web application. Which of the following solutions would be BEST to provide security, manageability,
and visibility into the platforms?
A. SIEM
B. DLP
C. CASB
D. SWG
Correct Answer: C
QUESTION 9
DRAG DROP
A security administrator has been tasked with implementing controls that meet management goals. Drag and drop the
appropriate control used to accomplish the account management goal. Options may be used once or not at all.
Select and Place:
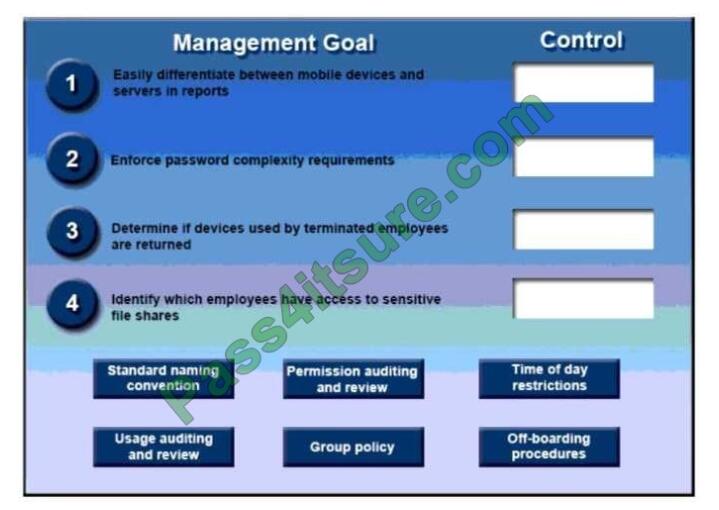
Correct Answer:
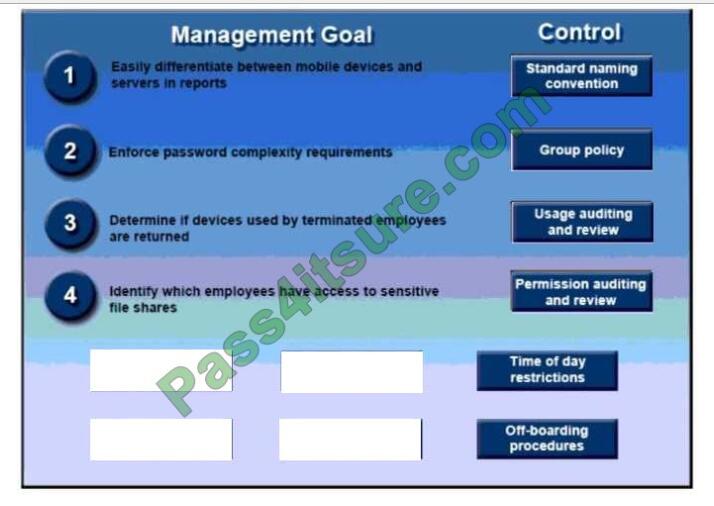
QUESTION 10
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing
websites.
INSTRUCTIONS
Click on each firewall to do the following:
1.
Deny cleartext web traffic.
2.
Ensure secure management protocols are used.
3.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
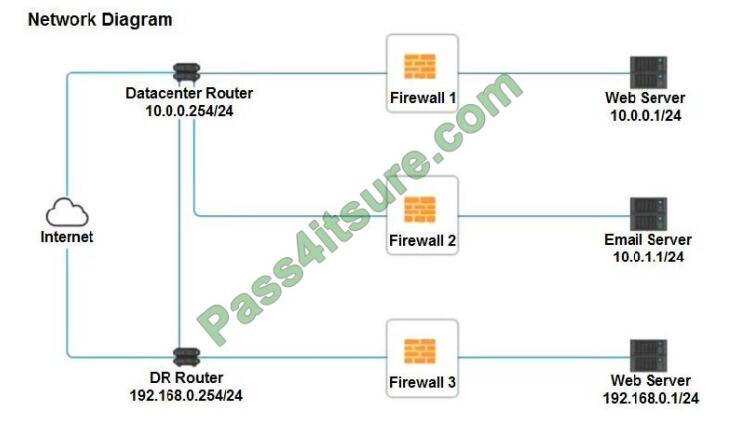
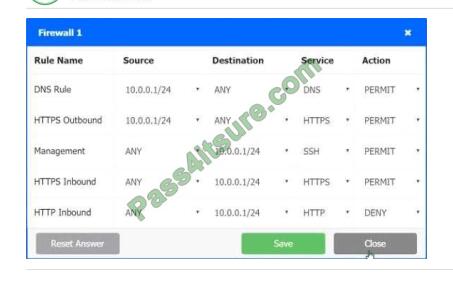
Firewall 1
Hot Area:
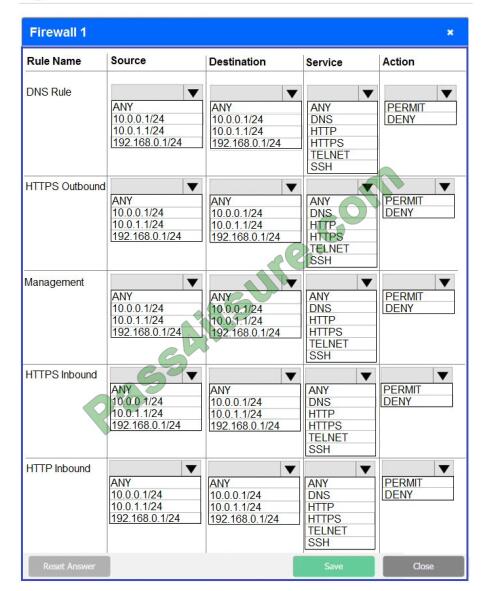
Correct Answer:
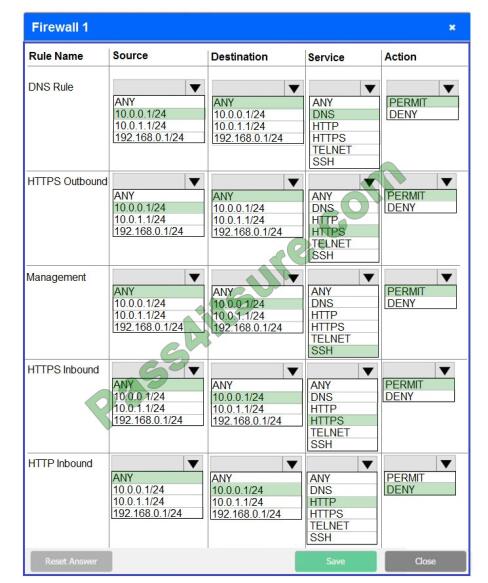
In Firewall 1, HTTP inbound Action should be DENY. As shown below
QUESTION 11
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on
user devices. Which of the following solutions would BEST support the policy?
A. Mobile device management
B. Full-device encryption
C. Remote wipe
D. Biometrics
Correct Answer: A
QUESTION 12
An organization has hired a new remote workforce. Many new employees are reporting that they are unable to access
the shared network resources while traveling. They need to be able to travel to and from different locations on a weekly
basis. Shared offices are retained at the headquarters location. The remote workforce will have identical file and system
access requirements, and must also be able to log in to the headquarters location remotely. Which of the following
BEST represent how the remote employees should have been set up initially? (Select TWO).
A. User-based access control
B. Shared accounts
C. Group-based access control
D. Mapped drives
E. Individual accounts
F. Location-based policies
Correct Answer: CE
QUESTION 13
DRAG DROP
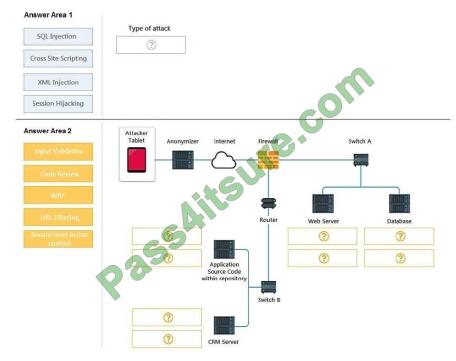
An attack has occurred against a company.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker\\’s tablet and reviewing the output.
(Answer Area 1)
Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of
future attacks by dragging them to the correct server. (Answer area 2) All objects will be used, but not all placeholders
may be
filled. Objects may only be used once. If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
Select and Place:
Correct Answer: 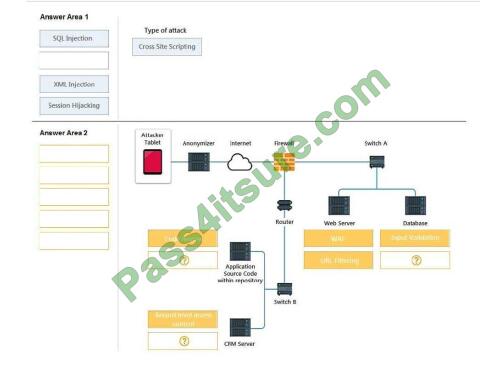
Latest CompTIA SY0-601 google drive
CompTIA SY0-601 pdf https://drive.google.com/file/d/1uN4EuabH-KOdfK7fisemo4B04FPodt5P/view?usp=sharing
Summarize:
This blog shares the latest CompTIA SY0-601 exam questions, and answers! CompTIA SY0-601 pdf!
You can also practice the test online! Pass4itsure is the industry leader! Go https://www.pass4itsure.com/sy0-601.html Help you successfully pass the CompTIA SY0-601 exam.
ps.
Free CompTIA SY0-601 dumps pdf download: https://drive.google.com/file/d/1uN4EuabH-KOdfK7fisemo4B04FPodt5P/view?usp=sharing