To help you successfully pass the CompTIA Security+ 2022 exam, we have updated the SY0-601 dumps, Pass4itSure SY0-601 dumps is a valid material for you to prepare for the SY0-601 exam.
CompTIA SY0-601 dumps – CompTIA Security+ exam preparation download page: https://www.pass4itsure.com/sy0-601.html SY0-601 PDF/ SY0-601 VCE instantly available for download. You will have 640+ exam questions and answers to prepare for your SY0-601 exam.
What are the most questioned about the SY0-601 exam?

1. What is the SY0-601 exam?
It is a globally recognized certification that demonstrates the competence of safety concepts and best practices. Successful candidates will have the knowledge and skills to prevent, detect, and mitigate systems and cyberattacks.
2. How many questions are there in the SY0-601 exam?
90 questions.
3. How long is the exam time?
90 minutes.
4. What is the best material to prepare for the CompTIA Security+ SY0-601 exam?
The Pass4itSure SY0-601 dumps, which helps you understand the key concepts covered in the exam and provides you with practice questions to help you test your knowledge, is the best preparation material for the CompTIA Security+ exam. It covers a wide variety of topics, so it’s important to have good learning materials. In the following, we will provide you with some security + exam questions and answers (free) to help you prepare.
5. Passing score?
| Passing Score | 750 (on a scale of 100-900) |
6. SY0-601 exam price
$381 USD
CompTIA Security+ 2022
SY0-601 free dumps Q&A
QUESTION # 1
A security administrator suspects there may be unnecessary services running on a server. Which of the following tools will the administrator MOST likely use to confirm the suspicions?
A. Nmap
B. Wireshark
C. Autopsy
D. DNSEnum
Correct Answer: A
https://nmap.org/book/man-version-detection.html
NMAP scans running services and can tell you what services are running
QUESTION # 2
Which of the following would be MOST effective to contain a rapidly attack that is affecting a large number of organizations?
A. Machine learning
B. DNS sinkhole
C. Blocklist
D. Honeypot
Correct Answer: D
QUESTION # 3
A forensics investigator is examining a number of unauthorized payments that were reported on the 00mpany\’s website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
Which of the following will the forensics investigator MOST likely determine has occurred?
A. SQL injection
B. CSRF
C. XSS
D. XSRF
Correct Answer: D
QUESTION # 4
A user recent an SMS on a mobile phone that asked for bank delays. Which of the following social-engineering techniques was used in this case?
A. SPIM
B. Vishing
C. Spear phishing
D. Smishing
Correct Answer: D
QUESTION # 5
A security administrator checks the table of a network switch, which shows the following output:

Which of the following is happening to this switch?
A. MAC Flooding
B. DNS poisoning
C. MAC cloning
D. ARP poisoning
Correct Answer: A
QUESTION # 6
The facilities supervisor for a government agency is concerned about unauthorized access to environmental systems in the event the staff WiFi network is breached. Which of the blowing would BEST address this security concern?
A. install a smart meter on the staff WiFi.
B. Place the environmental systems in the same DHCP scope as the staff WiFi.
C. Implement Zigbee on the staff WiFi access points.
D. Segment the staff WiFi network from the environmental systems network.
Correct Answer: D
QUESTION # 7
A user recently entered a username and password into a recruiting application website that had been forged to look like the legitimate site Upon investigation, a security analyst the identifies the following:
1. The legitimate websites IP address is 10.1.1.20 and eRecruit local resolves to the IP
2. The forged website\’s IP address appears to be 10.2.12.99. based on NetFtow records
3. AH three at the organization\’s DNS servers show the website correctly resolves to the legitimate IP
4. DNS query logs show one of the three DNS servers returned a result of 10.2.12.99 (cached) at the approximate time of the suspected compromise. Which of the following MOST likely occurred?
A. A reverse proxy was used to redirect network traffic
B. An SSL strip MITM attack was performed
C. An attacker temporarily pawned a name server
D. An ARP poisoning attack was successfully executed
Correct Answer: B
QUESTION # 8
DRAG DROP
Drag the items on the left to show the different types of security for the shown devices. Not all fields need to be filled. Not all items need to be used.
Correct Answer:
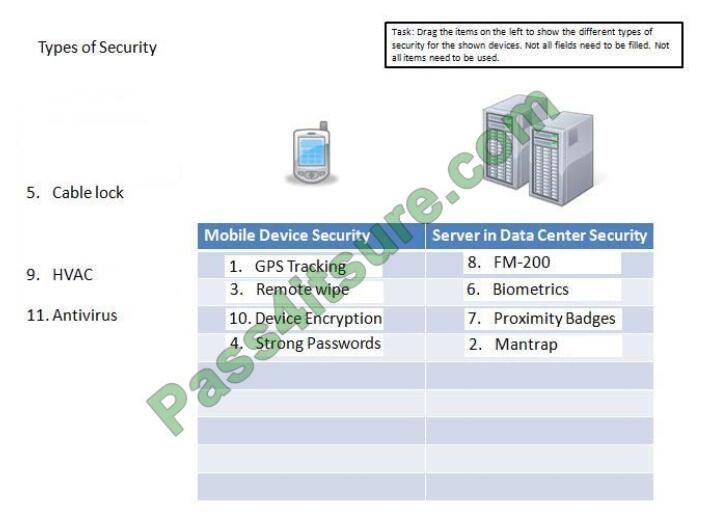
For mobile devices, at bare minimum you should have the following security measures in place: Screen lock, Strong password, Device encryption, Remote wipe/Sanitation, voice encryption, GPS tracking, Application control, Storage segmentation, Asset tracking as well as Device Access control.
For servers in a data center your security should include: Fire extinguishers such as FM200 as part of fire suppression;
Biometric, proximity badges, mantraps, HVAC, cable locks;
these can all be physical security measures to control access to the server.
References:
Dulaney, Emmett and Chuck Eastton, CompTIA Security+ Study Guide, 6th Edition, Sybex, Indianapolis, 2014, p. 418
QUESTION # 9
An external forensics investigator has been hired to investigate a data breach at a large enterprise with numerous assets. It is known that the breach started in the DMZ and moved to the sensitive information, generating multiple logs as the attacker traversed through the network? Which of the following will BEST assist with this investigation?
A. Perform a vulnerability scan to identify the weak spots
B. Use a packet analyzer to investigate the NetFlow traffic
C. Check the SIEM to review the correlated logs
D. Require access to the routers to view current sessions
Correct Answer: C
QUESTION # 10
A cybersecurity administrator needs to add disk redundancy for a critical server. The solution must have a two- drive failure for better fault tolerance. Which of the following RAID levels should the administrator select?
A. 0
B. 1
C. 5
D. 6
Correct Answer: B
QUESTION # 11
A security analyst Is hardening a Linux workstation and must ensure It has public keys forwarded to remote systems for secure login Which of the following steps should the analyst perform to meet these requirements? (Select TWO).
A. Forward the keys using ssh-copy-id.
B. Forward the keys using scp.
C. Forward the keys using ash -i.
D. Forward the keys using openssl -s.
E. Forward the keys using ssh-keyger.
Correct Answer: AD
QUESTION # 12
A recent security assessment revealed that an actor exploited a vulnerable workstation within an organization and has persisted on the network for several months. The organization realizes the need to reassess Its security. Strategy for mitigating risks within the perimeter.
Which of the following solutions would BEST support the organization\’s strategy?
A. FIM
B. DLP
C. EDR
D. UTM
Correct Answer: D
QUESTION # 13
Several universities are participating in a collaborative research project and need to share compute and storage resources. Which of the following cloud deployment strategies would BEST meet this need?
A. Private
B. C. Public
C. Hybrid
Correct Answer: A
Community cloud storage is a variation of the private cloud storage model, which offers cloud solutions for specific businesses or communities. In this model, cloud storage providers offer their cloud architecture, software and other development tools to meet the requirements of the community.
A community cloud in computing is a collaborative effort in which infrastructure is shared between several organizations from a specific community with common concerns (security, compliance, jurisdiction, etc.), whether managed internally or by a third-party and hosted internally or externally.
The free SY0-601 exam Q&A can be downloaded online: https://drive.google.com/file/d/1JP1Ec9PioOGhqNrU75ff8ZBrRKR7ssTH/view?usp=sharing
Also want to read more, SY0-601 exam questions, this website.