![CAS-004 Dumps Pdf Best [Resources]](https://www.downloadzpdf.com/wp-content/uploads/2022/01/CAS-004-Dumps-Pdf-Best-Resources.jpg)
…CAS-004 dumps pdf, It’s hard to find.
That doesn’t mean we can’t bring them together! Read on to learn about the latest CompTIA CAS-004 dumps pdf updates you really need to know, including:
- [google drive] CompTIA CAS-004 dumps pdf
- The newly released CompTIA CAS-004 practice test is online
- Will the CompTIA CAS-004 dumps pdf help me pass the exam?
- Are the CompTIA Advanced Security Practitioner (CASP+) exam questions and answers up to date?
Keep reading and get what you want.
CompTIA Advanced Security Practitioner (CASP+) CAS-004 pdf free
[google drive] https://drive.google.com/file/d/1e7Ay8uzQBz_-F86mloF4v4RDMGMk9JVf/view?usp=sharing
New CompTIA CAS-004 dumps update actual exam questions
Q# 1
Click on the exhibit buttons to view the four messages.
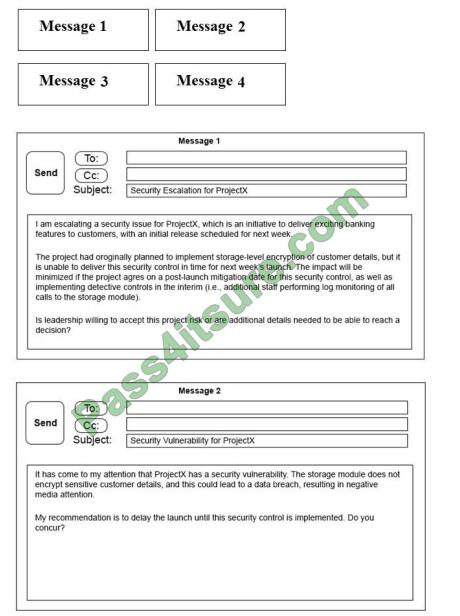
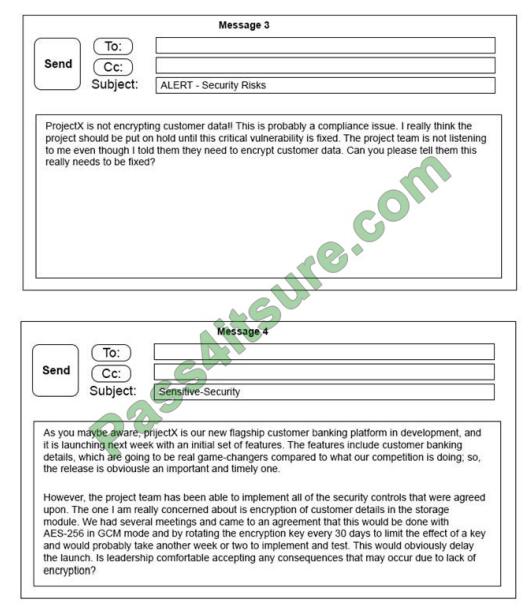
A security architect is working with a project team to deliver an important service that stores and processes customer banking details. The project, internally known as ProjectX, is due to launch its first set of features publicly within a week, but the team has not been able to implement encryption-at-rest of the customer records.
The security architect is drafting an escalation email to senior leadership.
Which of the following BEST conveys the business impact for senior leadership?
A. Message 1
B. Message 2
C. Message 3
D. Message 4
Correct Answer: D
Q# 2
A secure facility has a server room that currently is controlled by a simple lock and key. and several administrators have copies of the key. To maintain regulatory compliance, a second lock, which is controlled by an application on the administrators\’ smartphones, is purchased and installed.
The application has various authentication methods that can be used. The criteria for choosing the most appropriate method are:
1. It cannot be invasive to the end-user
2. It must be utilized as a second factor.
3. Information sharing must be avoided
4. It must have a low false acceptance rate
Which of the following BEST meets the criteria?
A. Facial recognition
B. Swipe pattern
C. Fingerprint scanning
D. Complex passcode
E. Token card
Correct Answer: C
Q# 3
A security engineer estimates the company\’s popular web application experiences 100 attempted breaches per day. In the past four years, the company\’s data has been breached two times. Which of the following should the engineer report as the ARO for successful breaches?
A. 0.5
B. 8
C. 50
D. 36,500
Correct Answer: A
Q# 4
A company\’s IT department currently performs traditional patching, and the servers have significant longevity that may span over five years. A security architect is moving the company toward an immune server architecture in which servers are replaced rather than patched.
Instead of having static servers for development, test, and production, the severs will move from environment to environment dynamically.
Which of the following are required to move to this type of architecture? (Select Two.)
A. Network segmentation
B. Forward proxy
C. Netflow
D. Load balancers
E. Automated deployments
Correct Answer: BD
Q# 5
A security engineer is assessing a new IoT product. The product interfaces with the ODBII port of a vehicle and uses a Bluetooth connection to relay data to an onboard data logger located in the vehicle. The data logger can only transfer data over a custom USB cable.
The engineer suspects a relay attack is possible against the cryptographic implementation used to secure messages between segments of the system. Which of the following tools should the engineer use to confirm the analysis?
A. Binary decompiler
B. Wireless protocol analyzer
C. Log analysis and reduction tools
D. Network-based fuzzer
Correct Answer: B
Q# 6
To prepare for an upcoming audit, the Chief Information Security Officer (CISO) asks for all 1200 vulnerabilities on production servers to be remediated. The security engineer must determine which vulnerabilities represent real threats that can be exploited so resources can be prioritized to migrate the most dangerous risks.
The CISO wants the security engineer to act in the same manner as would an external threat while using vulnerability scan results to prioritize any actions.
Which of the following approaches is described?
A. Blue team
B. Red team
C. Black box
D. White team
Correct Answer: C
Q# 7
An employee decides to log into an authorized system The system does not prompt the employee for authentication prior to granting access to the console, and it cannot authenticate the network resources. Which of the following attack types can this lead to if it is not mitigated?
A. Memory leak
B. Race condition
C. Smurf
D. Deadlock
Correct Answer: C
Reference: https://www imperva com/learn/ddos/smurf-attack-ddos/
Q# 8
A security analyst is reviewing the following packet capture of communication between a host and a company\\’s router:

Which of the following actions should the security analyst take to remove this vulnerability?
A. Update the router code
B. Implement a router ACL
C. Disconnect the host from the network
D. Install the latest antivirus definitions
E. Deploy a network-based IPS
Correct Answer: B
Q# 9
A mature organization with legacy information systems has incorporated numerous new processes and dependencies to manage security as its networks and infrastructure are modernized. The Chief Information Office has become increasingly frustrated with frequent releases, stating that the organization needs everything to work completely, and the vendor should already have those desires built into the software product.
The vendor has been in constant communication with personnel and groups within the organization to understand its business process and capture new software requirements from users. Which of the following methods of software development is this organization\’s configuration management process using?
A. Agile
B. SDL
C. Waterfall
D. Joint application development
Correct Answer: A
In agile software development, teams of programmers and business experts work closely together, using an iterative approach.
Q# 10
A popular commercial virtualization platform allows for the creation of virtual hardware. To virtual machines, this virtual hardware is indistinguishable from real hardware. By implementing virtualized TPMs, which of the following trusted system concepts can be implemented?
A. Software-based root of trust
B. Continuous chain of trust
C. Chain of trust with a hardware root of trust
D. Software-based trust anchor with no root of trust
Correct Answer: C
A Trusted Platform Module (TPM) is a microchip designed to provide basic security-related functions, primarily involving encryption keys. The TPM is usually installed on the motherboard of a computer, and it communicates with the remainder of the system by using a hardware bus.
A vTPM is a virtual Trusted Platform Module; a virtual instance of the TPM.
IBM extended the current TPM V1.2 command set with virtual TPM management commands that allow us to create and delete instances of TPMs. Each created instance of a TPM holds an association with a virtual machine (VM) throughout its lifetime on the platform.
The TPM is the hardware root of trust. Chain of trust means to extend the trust boundary from the root(s) of trust, in order to extend the collection of trustworthy functions. Implies/entails transitive trust.
Therefore a virtual TPM is a chain of trust from the hardware TPM (the root of trust).
Q# 11
Following a complete outage of the electronic medical record system for more than 18 hours, the hospital\\’s Chief Executive Officer (CEO) has requested that the Chief Information Security Officer (CISO) perform an investigation into the possibility of a disgruntled employee causing the outage maliciously.
To begin the investigation, the CISO pulls all event logs and device configurations from the time of the outage. The CISO immediately notices the configuration of a top-of-rack switch from one day prior to the outage does not match the configuration that was in place at the time of the outage.
However, none of the event logs show who changed the switch configuration, and seven people have the ability to change it. Because of this, the investigation is inconclusive.
Which of the following processes should be implemented to ensure this information is available for future investigations?
A. Asset inventory management
B. Incident response plan
C. Test and evaluation
D. Configuration and change management
Correct Answer: D
Q# 12
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded and unmanaged HVAC controller, which is used to monitor the company\’s datacenter
Port state
161/UDP open
162/UDP open
163/TCP open
The enterprise monitoring service requires SNMP and SNMP TRAP connectivity to operate. Which of the following should the security administrator implement to harden the system?
A. Patch and restart the unknown services.
B. Segment and firewall the controller\’s network
C. Disable the unidentified service on the controller.
D. Implement SNMPv3 to secure communication.
E. Disable TCP/UDP PORTS 161 THROUGH 163
Correct Answer: D
Can a CompTIA CAS-004 (CASP+) dumps pdf help you pass the exam?
Must be affirmative. Using a real and complete CompTIA CAS-004 dumps pdf (Get it here https://www.pass4itsure.com/cas-004.html) will help you successfully pass the CompTIA Advanced Security Practitioner certification CAS-004 exam.
CompTIA Advanced Security Practitioner (CASP+) exam questions and answers up to date?
Yes, the free CompTIA Advanced Security Practitioner (CASP+) questions are part of the Pass4itSure CAS-004 dumps. To pass the exam 100%, please obtain the CAS-004 exam dumps immediately.
full CAS-004 dumps pdf https://www.pass4itsure.com/cas-004.html (Q&As: 869).
To pass the CompTIA CAS-004 exam 2022, recommended actions:
Get the correct CAS-004 dumps pdf, practice hard, improve yourself, take the exam, and successfully earn the CompTIA Advanced Security Practitioner certification.
Stay tuned for more updates!