This article mainly guides you to study for the CySA+ CS0-003 exam correctly, with the latest CySA+ CS0-003 exam questions online and a comprehensive study guide, so that you can easily pass the CompTIA CySA+ certification CS0-003 exam.
The following content is divided into three main parts:
- CySA+ CS0-003 exam content details
- Up-to-date CompTIA CySA+ CS0-003 study guide
- Free CompTIA CySA+ CS0-003 exam questions
CompTIA CySA+ CS0-003 exam content details
How to Prepare for the CompTIA CS0-003 Exam? Appropriate purchase of high-quality study materials (e.g. Pass4itSure CySA+ CS0-003 exam question resources, which cover all aspects of the exam and provide practice questions with explanations PDF+VCE)
How many questions are in the CS0-003 exam? Up to 85 pcs
How long is the exam? 165 minutes
What are the question types in the CySA+ CS0-003 exam? Multiple-choice and performance-based forms
What is the required score to pass? 750 points (100-900 points)
What experience is required to take the CS0-003 exam? Knowledge of Network+, Security+, or equivalent. At least 4 years of hands-on experience as an Incident Response Analyst or Security Operations Center (SOC) Analyst, or equivalent.
What positions are available after passing the CS0-003 exam to obtain the CompTIA CySA+ certification? Full-Source Analyst, Warning Analyst, Forensic Analyst, Cyber Defense Forensics Analyst, Cyber Crime Investigator, System Security Analyst, Cyber Defense Analyst, Cyber Defense Incident Responder, Vulnerability Assessment Analyst, Security Control Assessor
How is the CS0-003 exam different from the retired CS0-002 exam? The test areas are different, from five to four, which has been streamlined.
Why is the CySA+ exam set for retirement around three years later? That’s because the market is changing, and only constant updates can incorporate the latest trends and security threats into the latest version. The updated CS0-003 focuses more on the latest security analyst techniques.
What’s new in the CS0-003 exam? Current trends, cloud, and mobile, threat intelligence
Has there been any change to the CySA+ certification pathway? No, the same as CS0-002.
Which certifications are highly relevant to the CompTIA CySA+ certification? EC-Council Certified Security Analyst (ECSA), GIAC Continuous Monitoring Certification (GMON), Certified Information Systems Auditor (CISA)
Are there any discounts, such as discount codes, for CompTIA CySA+ certification learning materials? Yes, CompTIA’s official code: is SAVE15JUNE Get 15% off. Pass4itSure CySA+ CS0-003 exam question resources are also available with code: save10 for a 10% discount.
CompTIA CySA+ CS0-003 study guide (Updated)
Everything is designed to help you pass the CS0-003 exam.
How can I learn CompTIA CySA+ CS0-003? You should follow this step:
- Research the content of the official study guide
- Practice with Pass4itSure CySA+ CS0-003 exam questions
- Timely review
- Take a formal exam
As an added point, you can use various resources (textbooks, online courses, practice exams, and video tutorials) to prepare, which is more effective, depending on the individual’s situation—not limited to what is said above. Timely review contributes to your success, which is important for passing the exam.
Free CompTIA CySA+ CS0-003 exam questions
Provider: Pass4itSure
Number of Questions: 1-15
Last updated: free CS0-003 exam questions
Certifications: CompTIA
Question 1:
A company creates digitally signed packages for its devices. Which of the following best describes the method by which the security packages are delivered to the company\’s customers?
A. Antitamper mechanism
B. SELinux
C. Trusted firmware updates
D. eFuse
Correct Answer: C
Trusted firmware updates are a method by which security package” customers. Trusted firmware updates are digitally signed packages that contain software updates or patches for devices, such as routers, switches, or firewalls. Trusted firmware updates can help to ensure the authenticity and integrity of the packages by verifying the digital signature of the sender and preventing unauthorized or malicious modifications to the packages. https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_trustsec/configuration/xe-16/sec-usr-trustsec-xe-16-book/sec-trust-firm-upd.html
Question 2:
An analyst needs to forensically examine a Windows machine that was compromised by a threat actor. Intelligence reports state this specific threat actor is characterized by hiding malicious artifacts, especially with alternate data streams. Based on this intelligence, which of the following BEST explains alternate data streams?
A. A different way data can be streamlined if the user wants to use less memory on a Windows system for forking resources.
B. A way to store data on an external drive attached to a Windows machine that is not readily accessible to users.
C. A Windows attribute that provides for forking resources and is potentially used to hide the presence of secret or malicious files inside the file records of a benign file.
D. A Windows attribute that can be used by attackers to hide malicious files within system memory.
Correct Answer: C
Question 3:
Which of the following is often used to keep the number of alerts to a manageable level when establishing a process to track and analyze violations?
A. Log Retention
B. Log Rotation
C. Maximum log size
D. Threshold value
Correct Answer: D
A threshold value is a parameter that defines the minimum or maximum level of a metric or event that triggers an alert. For example, a threshold value can be set to alert when the number of failed login attempts exceeds 10 in an hour, or when the CPU usage drops below 20% for more than 15 minutes. By setting a threshold value, the process can filter out irrelevant or insignificant alerts and focus on the ones that indicate a potential problem or anomaly. A threshold value can help to reduce the noise and false positives in the alert system and improve the efficiency and accuracy of the analysis
Question 4:
The Chief Information Security Officer is directing a new program to reduce attack surface risks and threats as part of a zero-trust approach. The IT security team is required to come up with priorities for the program. Which of the following is the best priority based on common attack frameworks?
A. Reduce the administrator and privileged access accounts
B. Employ a network-based IDS
C. Conduct thorough incident response
D. Enable SSO to enterprise applications
Correct Answer: A
The best priority based on common attack frameworks for a new program to reduce attack surface risks and threats as part of a zero trust approach is to reduce the administrator and privileged access accounts. Administrator and privileged access accounts are accounts that have elevated permissions or capabilities to perform sensitive or critical tasks on systems or networks, such as installing software, changing configurations, accessing data, or granting access.
Reducing the administrator and privileged access accounts can help minimize the attack surface, as it can limit the number of potential targets or entry points for attackers, as well as reduce the impact or damage of an attack if an account is compromised.
Question 5:
Which of the following is the greatest security concern regarding ICS?
A. The involved systems are generally hard to identify.
B. The systems are configured for automatic updates, leading to device failure.
C. The systems are oftentimes air-gapped, leading to fileless malware attacks.
D. Issues on the systems cannot be reversed without rebuilding the systems.
Correct Answer: D
Industrial control systems (ICS) are systems that monitor and control physical processes, such as power generation, water treatment, manufacturing, and transportation. ICSs are often critical for public safety and national security, and therefore a prime target for cyberattacks. One of the greatest security concerns regarding ICS is that issues on the systems cannot be reversed without rebuilding the systems.
This means that any damage or disruption caused by an attack can have long-lasting and catastrophic consequences for the physical infrastructure and human lives. The other options are not true or not specific to ICS. CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0-002), page 13; https://www.us-cert.gov/ics/What-are-Industrial-Control-Systems
Question 6:
A security analyst wants to capture large amounts of network data that will be analyzed at a later time. The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called “packet capture.” The capture must be as efficient as possible, and the analyst wants to minimize the likelihood that packets will be missed. Which of the following commands will best accomplish the analyst\’s objectives?
A. tcpdump -w packet capture
B. tcpdump -a packet capture
C. tcpdump -n packet capture
D. nmap -v > packet capture
E. nmap -oA > packet capture
Correct Answer: A
The tcpdump command is a network packet analyzer tool that can capture and display network traffic. The -w option specifies a file name to write the captured packets to, in a binary format that can be read by tcpdump or other tools later. This option is useful for capturing large amounts of network data that will be analyzed at a later time, as the question requires.
The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called “. The capture must be as efficient as possible, and the -w option minimizes the processing and output overhead of tcpdump, reducing the likelihood that packets will be missed.
Question 7:
The vulnerability analyst reviews threat intelligence regarding emerging vulnerabilities affecting workstations that are used within the company: Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?
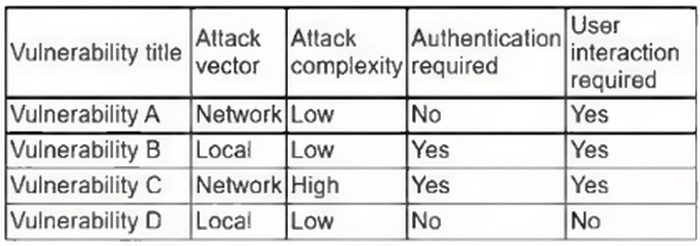
A. Vulnerability A
B. Vulnerability B
C. Vulnerability C
D. Vulnerability D
Correct Answer: C
In this scenario, Vulnerability C is the one that should most concern the analyst, as it has a network attack vector, high attack complexity, and requires authentication and user interaction. This means that an attacker could exploit this vulnerability remotely, without the need for direct user interaction, making it a more critical threat in this context.
In this scenario, Vulnerability C is the one that should most concern the analyst, as it has a network attack vector, high attack complexity, and requires authentication and user interaction. This means that an attacker could exploit this vulnerability remotely, without the need for direct user interaction, making it a more critical threat in this context.
Question 8:
During an investigation, an analyst discovers the following rule in an executive\’s email client:

The executive is not aware of this rule. Which of the following should the analyst do first to evaluate the potential impact of this security incident?
A. Check the server logs to evaluate which emails were sent to.
B. Use the SIEM to correlate logging events from the email server and the domain server.
C. Remove the rule from the email client and change the password.
D. Recommend that the management team implement SPF and DKIM.
Correct Answer: C
Question 9:
A manufacturer has hired a third-party consultant to assess the security of an OT network that includes both fragile and legacy equipment.
Which of the following must be considered to ensure the consultant does not harm operations?
A. Employing Nmap Scripting Engine scanning techniques
B. Preserving the state of PLC ladder logic before scanning
C. Using passive instead of active vulnerability scans
D. Running scans during off-peak manufacturing hours
Correct Answer: C
Explanation: In environments with fragile and legacy equipment, passive scanning is preferred to prevent any potential disruptions that active scanning might cause.
When assessing the security of an Operational Technology (OT) network, especially one with fragile and legacy equipment, it \ is crucial to use passive instead of active vulnerability scans. Active scanning can sometimes disrupt the operation of sensitive or older equipment. Passive scanning listens to network traffic without sending probing requests, thus minimizing the risk of disruption.
Question 10
An analyst is examining events in multiple systems but is having difficulty correlating data points. Which of the following is most likely the issue with the system?
A. Access rights
B. Network segmentation
C. Time synchronization
D. Invalid playbook
Correct Answer: C
When examining events in multiple systems and having difficulty correlating data points, the most likely issue could be a lack of proper time synchronization across the systems. Time synchronization is crucial for accurate event correlation and forensic analysis, as it ensures that events are properly aligned in chronological order.
Question 11:
A security analyst at a company called ACME Commercial notices there is outbound traffic to a host IP that resolves to
A. This is a normal password change URL.
B. The security operations center is performing a routine password audit.
C. A new VPN gateway has been deployed.
D. A social engineering attack is underway.
Correct Answer: D
Question 12:
Which of the following techniques can help a SOC team reduce the number of alerts related to the internal security activities that the analysts have to triage?
A. Enrich the SIEM-ingested data to include all data required for triage.
B. Schedule a task to disable alerting when vulnerability scans are executing.
C. Filter all alarms in the SIEM with low severity.
D. Add a SOAR rule to drop irrelevant and duplicated notifications.
Correct Answer: B
Question 13:
An organization\’s threat intelligence team notes a recent trend in adversary privilege escalation procedures. Multiple threat groups have been observed utilizing native Windows tools to bypass system controls and execute commands with privileged credentials. Which of the following controls would be most effective to reduce the rate of success of such attempts?
A. Set user account control protection to the most restrictive level on all devices
B. Implement MFA requirements for all internal resources
C. Harden systems by disabling or removing unnecessary services
D. Implement controls to block the execution of untrusted applications
Correct Answer: C
Question 14:
A recent audit of the vulnerability management program outlined the finding for increased awareness of secure coding practices. Which of the following would be best to address the finding?
A. Establish quarterly SDLC training on the top vulnerabilities for developers
B. Conduct a yearly inspection of the code repositories and provide the report to management.
C. Hire an external penetration test of the network
D. Deploy more vulnerability scanners for increased coverage
Correct Answer: A
The finding in the audit suggests a need to improve awareness of secure coding practices. The most appropriate action to address this finding is to provide training to the development team on secure coding practices.
Question 15:
An employee is no longer able to log in to an account after updating a browser. The employee usually has several tabs open in the browser. Which of the following attacks was most likely performed?
A. RFI
B. LFI
C. CSRF
D. XSS
Correct Answer: C
Explanation: The most likely attack that was performed is CSRF (Cross-Site Request Forgery). This is an attack that forces a user to execute unwanted actions on a web application in which they are currently authenticated1. If the user has several tabs open in the browser, one of them might contain a malicious link or form that sends a request to the web application to change the user\’s password, email address, or other account settings. The web application will not be able to distinguish between the legitimate requests made by the user and the forged requests made by the attacker.
As a result, the user will lose access to their account. To prevent CSRF attacks, web applications should implement some form of anti-CSRF tokens or other mechanisms that validate the origin and integrity of the requests2. These tokens are unique and unpredictable values that are generated by the server and embedded in the forms or URLs that perform state-changing actions.
The server will then verify that the token received from the client matches the token stored on the server before processing the request. This way, an attacker cannot forge a valid request without knowing the token value. Some other possible attacks that are not relevant to this scenario are: RFI (Remote File Inclusion) is an attack that allows an attacker to execute malicious code on a web server by including a remote file in a script.
This attack does not affect the user\’s browser or account settings. LFI (Local File Inclusion) is an attack that allows an attacker to read or execute local files on a web server by manipulating the input parameters of a script. This attack does not affect the user\’s browser or account settings. XSS (Cross-Site Scripting) is an attack that injects malicious code into a web page that is then executed by the user\’s browser.
This attack can affect the user\’s browser or account settings, but it requires the user to visit a compromised web page or click on a malicious link. It does not depend on having several tabs open in the browser.
Employment and development in CompTIA CySA+
Here we will focus on the job opportunities that may be available to CompTIA CySA+ certification holders, as well as the salary range you may receive after obtaining the certification.
CompTIA lists common positions for CySA+ certified professionals, such as Security Operations Center (SOC) Analyst, Vulnerability Analyst, Threat Intelligence Analyst, and Security Engineer. Because job opportunities are so much more relevant than that.
When looking for jobs that cite CySA+ on the popular job board Indeed, job titles such as “Security Analyst I” and “Cybersecurity Analyst” are listed. Salaries range from $60,000 up to well over $120,000.
ZipRecruiter reports that the national average annual income in the United States is $54,791, with 90% of them earning around $100,000 per year.
HowToNetwork.com reports that the average salary for CySA+ is similar to that of ZipRecruiter, with an annual salary of $60,000 or close.
However, it should be noted that this is related to the time of work experience, and those with experience can get a high salary.
When it comes to the development of CompTIA CySA+, the CompTIA CySA+ certification is a stepping stone to a promising career in cybersecurity, with the potential to provide a solid foundation of skills and knowledge for advancement to higher positions, and the importance cannot be overstated.
Conclusion
This article is about sharing questions about the new CompTIA CySA+ exam and how to study properly for the exam so that you can pass it successfully. Remember the order of preparing for the CompTIA CySA+ CS0-003 exam is: Study the official study guide content – Practice with Pass4itSure CySA+ CS0-003 exam questions (https://www.pass4itsure.com/cs0-003.html) – Review in time – Take the official exam.
Although the CompTIA CS0-003 exam is not easy, with correct study guidance, good study materials, and enough patience, it is still possible to get the CompTIA CySA+ certification.