The latest CompTIA CS0-002 exam questions can help you pass the exam! All questions are corrected
to ensure authenticity and effectiveness! Download the Pass4itsure CompTIA CS0-002 dumps https://www.pass4itsure.com/cs0-002.html (Q&As: 260).
[Latest PDF] Free CompTIA CS0-002 pdf dumps download from Google Drive: https://drive.google.com/file/d/1Ip7GoSI_oWrxox2HeKSIyX06Pi55ZQJA/view?usp=sharing
Share CompTIA CS0-002 practice test for free
QUESTION 1
During an investigation, a security analyst determines suspicious activity occurred during the night shift over the
weekend. Further investigation reveals the activity was initiated from an internal IP going to an external website. Which
of the following would be the MOST appropriate recommendation to prevent the activity from happening in the future?
A. An IPS signature modification for the specific IP addresses
B. An IDS signature modification for the specific IP addresses
C. A firewall rule that will block port 80 traffic
D. A firewall rule that will block traffic from the specific IP addresses
Correct Answer: D
QUESTION 2
A security analyst has been alerted to several emails that snow evidence an employee is planning malicious activities
that involve employee Pll on the network before leaving the organization. The security analysis BEST response would
be to coordinate with the legal department and:
A. the public relations department
B. senior leadership
C. law enforcement
D. the human resources department
Correct Answer: D
QUESTION 3
The inability to do remote updates of certificates. keys software and firmware is a security issue commonly associated
with:
A. web servers on private networks.
B. HVAC control systems
C. smartphones
D. firewalls and UTM devices
Correct Answer: B
QUESTION 4
A security manager has asked an analyst to provide feedback on the results of a penetration lest. After reviewing the
results the manager requests information regarding the possible exploitation of vulnerabilities Much of the following
information data points would be MOST useful for the analyst to provide to the security manager who would then
communicate the risk factors to senior management? (Select TWO)
A. Probability
B. Adversary capability
C. Attack vector
D. Impact
E. Classification
F. Indicators of compromise
Correct Answer: AD
QUESTION 5
A security analyst has discovered suspicious traffic and determined a host is connecting to a known malicious website.
The MOST appropriate action for the analyst to take would be lo implement a change request to:
A. update the antivirus software
B. configure the firewall to block traffic to the domain
C. add the domain to the blacklist
D. create an IPS signature for the domain
Correct Answer: B
QUESTION 6
An information security analyst is compiling data from a recent penetration test and reviews the following output:
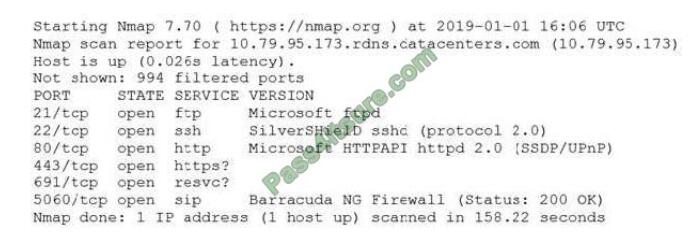
The analyst wants to obtain more information about the web-based services that are running on the target. Which of the
following commands would MOST likely provide the needed information?
A. ping -t 10.79.95.173.rdns.datacenters.com
B. telnet 10.79.95.173 443
C. ftpd 10.79.95.173.rdns.datacenters.com 443
D. tracert 10.79.95.173
Correct Answer: B
QUESTION 7
A threat feed notes malicious actors have been infiltrating companies and exfiltration data to a specific set of domains
Management at an organization wants to know if it is a victim Which of the following should the security analyst
recommend to identity this behavior without alerting any potential malicious actors?
A. Create an IPS rule to block these domains and trigger an alert within the SIEM tool when these domains are
requested
B. Add the domains to a DNS sinkhole and create an alert m the SIEM toot when the domains are queried
C. Look up the IP addresses for these domains and search firewall logs for any traffic being sent to those IPs over port
443
D. Query DNS logs with a SIEM tool for any hosts requesting the malicious domains and create alerts based on this
information
Correct Answer: D
QUESTION 8
An analyst is performing penetration testing and vulnerability assessment activities against a new vehicle automation
platform. Which of the following is MOST likely an attack vector that is being utilized as part of the testing and
assessment?
A. FaaS
B. RTOS
C. SoC
D. GPS
E. CAN bus
Correct Answer: E
QUESTION 9
A security analyst at a technology solutions firm has uncovered the same vulnerabilities on a vulnerability scan for a
long period of time. The vulnerabilities are on systems that are dedicated to the firm\\’s largest client. Which of the
following is MOST likely inhibiting the remediation efforts?
A. The parties have an MOU between them that could prevent shutting down the systems
B. There is a potential disruption of the vendor-client relationship
C. Patches for the vulnerabilities have not been fully tested by the software vendor
D. There is an SLA with the client that allows very little downtime
Correct Answer: D
QUESTION 10
An analyst wants to identify hosts that are connecting to the external FTP servers and what, if any, passwords are being
used. Which of the following commands should the analyst use?
A. tcpdump –X dst port 21
B. ftp ftp.server –p 21
C. nmap –o ftp.server –p 21
D. telnet ftp.server 21
Correct Answer: A
QUESTION 11
A forensic analyst took an image of a workstation that was involved in an incident To BEST ensure the image is not
tampered with me analyst should use:
A. hashing
B. backup tapes
C. a legal hold
D. chain of custody.
Correct Answer: D
QUESTION 12
A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely
targeting an organization\\’s financial assets. Which of the following is the BEST example of the level of sophistication
this threat actor is using?
A. Social media accounts attributed to the threat actor
B. Custom malware attributed to the threat actor from prior attacks
C. Email addresses and phone numbers tied to the threat actor
D. Network assets used in previous attacks attributed to the threat actor
E. IP addresses used by the threat actor for command and control
Correct Answer: D
QUESTION 13
A security analyst is responding to an incident on a web server on the company network that is making a large number
of outbound requests over DNS Which of the following is the FIRST step the analyst should take to evaluate this
potential indicator of compromise\\’?
A. Run an anti-malware scan on the system to detect and eradicate the current threat
B. Start a network capture on the system to look into the DNS requests to validate command and control traffic.
C. Shut down the system to prevent further degradation of the company network
D. Reimage the machine to remove the threat completely and get back to a normal running state.
E. Isolate the system on the network to ensure it cannot access other systems while evaluation is underway.
Correct Answer: A
Maybe you think it’s not enough. Here are the CompTIA CS0-002 practice questions updated in April https://www.downloadzpdf.com/share-free-comptia-cs0-002-exam-questions-and-comptia-cs0-002-dumps-pdf/ Hope to help you!
Latest CompTIA CS0-002 google drive
CompTIA CS0-002 pdf https://drive.google.com/file/d/1Ip7GoSI_oWrxox2HeKSIyX06Pi55ZQJA/view?usp=sharing
Summarize:
This blog shares the latest CompTIA CS0-002 exam questions, and answers! CompTIA CS0-002 pdf!
You can also practice the test online! Pass4itsure is the industry leader! https://www.pass4itsure.com/cs0-002.html Go Help you successfully pass the CompTIA CS0-002 exam.
ps.
Free CompTIA CS0-002 dumps pdf download: https://drive.google.com/file/d/1Ip7GoSI_oWrxox2HeKSIyX06Pi55ZQJA/view?usp=sharing