
The CompTIA Cloud+ CV0-004 exam was released on September 24, 2024, and aims to test the following six areas:
- Cloud architecture: 23%.
- Deployment: 19%.
- Security: 19%.
- Operations: 17%.
- Troubleshooting: 12%.
- DevOps fundamentals: 10%.
Compare CompTIA Cloud+ CV0-003 released in 2021:
- Deployment: 23%.
- Operations and support: 22%.
- Troubleshooting: 22%.
- Security: 20%.
- Cloud architecture and design: 13%.
Based on data comparison, it is not difficult to find that the main difference is the addition of the DevOps field. Other content CV0-004 goals will refocus on service availability and less on capacity planning. The CV0-003 content contains more information about the business and user needs, but this information is still well represented in CV0-004.
Overall, CompTIA’s commitment to keeping certifications current and forward-looking is undeniable, so how do candidates study to successfully pass the CompTIA Cloud+ CV0-004 exam?
- Be proficient in terminology and concepts
- CompTIA provides a rich certification training library
- Mock exam
- Laboratory
- Online courses
To sum up, the mock exam is one of the necessary conditions for you to pass the CompTIA Cloud+ CV0-004 exam. Next, we will share the CompTIA Cloud+ CV0-004 certification exam materials for free:
CompTIA Cloud+ CV0-004 exam questions and answers
| From | Number of exam questions | Full |
| Pass4itsure | 15 Q&As | 285 Q&As |
Question 1:
An administrator is setting up a cloud backup solution that requires the following features:
4.
Cost effective
5.
Granular recovery
6.
Multilocation
Which of the following backup types best meets these requirements?
A. Off-site, full, incremental, and differential
B. Cloud site, full, and differential
C. On-site. full, and incremental
D. On-site. full, and differential
Correct Answer: A
An off-site cloud backup solution that offers full, incremental, and differential backups would best meet the requirements of being cost-effective, allowing granular recovery, and supporting multi-location storage. This combination allows for
comprehensive backup strategies that can be tailored to the company\’s needs while optimizing storage costs.
References: Backup strategies, including full, incremental, and differential backups, are an integral part of data management and protection strategies discussed in the CompTIA Cloud+ objectives.
Question 2:
Which of the following would allow a cloud engineer to flatten a deeply nested JSON log to improve readability for analysts?
A. Grafana
B. Kibana
C. Elasticsearch
D. Logstash
Correct Answer: D
Logstash can be used to flatten a deeply nested JSON log, which would improve readability for analysts. Logstash is a data processing pipeline that ingests data from various sources, transforms it, and then sends it to a “stash” like Elasticsearch. References: CompTIA Cloud+ Study Guide (V0-004) – Chapter on Cloud Data Management
Question 3:
A company that performs passive vulnerability scanning at its transit VPC has detected a vulnerability related to outdated web-server software on one of its public subnets.
Which of the following can the use to verify if this is a true positive with the LEAST effort and cost? (Select TWO).
A. A network-based scan
B. An agent-based scan
C. A port scan
D. A red-team exercise
E. A credentialed scan
F. A blue-team exercise
G. Unknown environment penetration testing
Correct Answer: BE
The correct answer is B and E. An agent-based scan and a credentialed scan can help verify if the vulnerability related to outdated web-server software is a true positive with the least effort and cost.
An agent-based scan is a type of vulnerability scan that uses software agents installed on the target systems to collect and report data on vulnerabilities.
This method can provide more accurate and detailed results than a network-based scan, which relies on network traffic analysis and probes1.
An agent-based scan can also reduce the network bandwidth and performance impact of scanning, as well as avoid triggering false alarms from intrusion detection systems2.
A credentialed scan is a type of vulnerability scan that uses valid login credentials to access the target systems and perform a more thorough and comprehensive assessment of their configuration, patch level, and vulnerabilities.
A credentialed scan can identify vulnerabilities that are not visible or exploitable from the network level, such as missing updates, weak passwords, or misconfigured services3.
A credentialed scan can also reduce the risk of false positives and false negatives, as well as avoid causing damage or disruption to the target systems3.
A network-based scan, a port scan, a red-team exercise, a blue-team exercise, and unknown environment penetration testing are not the best options to verify if the vulnerability is a true positive with the least effort and cost.
A network-based scan and a port scan may not be able to detect the vulnerability if it is not exposed or exploitable from the network level.
A red-team exercise, a blue-team exercise, and unknown environment penetration testing are more complex, time-consuming, and costly methods that involve simulating real-world attacks or defending against them.
These methods are more suitable for testing the overall security posture and resilience of an organization, rather than verifying a specific vulnerability4.
Question 4:
A security engineer recently discovered a vulnerability in the operating system of the company VMs. The operations team reviews the issue and decides all VMs need to be updated from version 3.4.0 to 3.4.1. Which of the following best describes the type of update that will be applied?
A. Consistent
B. Major
C. Minor
D. Ephemeral
Correct Answer: C
The update from version 3.4.0 to 3.4.1 is considered a minor update, typically involving small bug fixes or security patches that do not include major feature changes or improvements. References: CompTIA Cloud+ Study Guide (V0-004) – Chapter on Systems Management
Question 5:
An IT professional is selecting the appropriate cloud storage solution for an application that has the following requirements:
The owner of the objects should be the object writer. The storage system must enforce TLS encryption.
Which of the following should the IT professional configure?
A. A bucket
B. A CIFS endpoint
C. A SAN
D. An NFS mount
Correct Answer: A
A bucket Comprehensive A bucket is a cloud storage solution that allows users to store and access objects, such as files, images, videos, etc.
A bucket is typically associated with object storage services, such as Amazon S3, Google Cloud Storage, or Microsoft Azure Blob Storage123.
A bucket has the following characteristics that match the requirements of the application: The owner of the objects is the object writer. This means that the user who uploads or writes an object to the bucket becomes the owner of that object and can control its access permissions456.
The storage system enforces TLS encryption. This means that the data in transit between the client and the bucket is encrypted using the Transport Layer Security (TLS) protocol, which provides security and privacy for the communication.
A CIFS endpoint, a SAN, and an NFS mount are not cloud storage solutions, but rather network protocols or architectures that enable access to storage devices
Question 6:
A company requests that its cloud administrator provision virtual desktops for every user. Given the following information:
1.
One hundred users are at the company.
2.
A maximum of 30 users work at the same time.
3.
Users cannot be interrupted while working on the desktop.
Which of the following strategies will reduce costs the most?
A. Provisioning VMs of varying sizes to match user needs
B. Configuring a group of VMs to share with multiple users
C. Using VMs that have spot availability
D. Setting up the VMs to turn off outside of business hours at night
Correct Answer: D
Setting up the VMs to turn off outside of business hours at night will reduce costs the most, especially since a maximum of 30 users work at the same time and users cannot be interrupted while working. This approach ensures that resources are used only when necessary.
References: Cost management and efficient resource utilization strategies like scheduling VMs to turn off during idle times are discussed within the financial management aspects of cloud services in the CompTIA Cloud+ exam objectives.
Question 7:
A cloud administrator is choosing a backup schedule for a new application platform that creates many small files. The backup process impacts the performance of the application, and backup times should be minimized during weekdays.
Which of the following backup types best meets the weekday requirements?
A. Database dump
B. Differential
C. Incremental
D. Full
Correct Answer: C
Question 8:
SIMULATION
An e-commerce company is migrating from an on-premises private cloud environment to a public cloud IaaS environment. You are tasked with right-sizing the environment to save costs after the migration. The company\’s requirements are to provide a 20% overhead above the average resource consumption, rounded up.
INSTRUCTIONS
Review the specifications and graphs showing resource usage for the web and database servers. Determine the average resource usage and select the correct specifications from the available drop-down options.
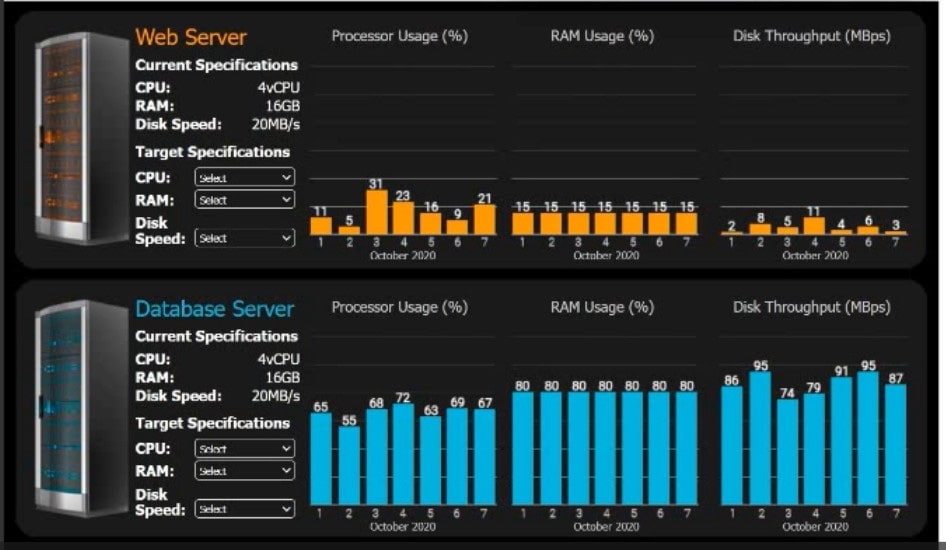
A. Check the for the complete Solution.
B. PlaceHolder
C. PlaceHolder
D. PlaceHolder
Correct Answer: A
For the Web Server: CPU: 2 vCPUs RAM: 2GB Disk Speed: 10MBps For the Database Server: CPU: 6 vCPUs RAM: 128GB Disk Speed: 110MBps These selections are based on maintaining a 20% overhead above the average resource consumption and rounding up to the next available option in the dropdowns provided.
Question 9:
A cloud engineer is developing an operating expense report that will be used to purchase various cloud billing models for virtual machine instances. The cloud billing model must meet the following requirements:
1.
The instance cannot be ephemeral.
2.
The minimum life cycle of the instance is expected to be five years.
3.
The software license is charged per physical CPU count.
Which of the following models would best meet these requirements?
A. Dedicated host
B. Spot instance
C. Pay-as-you-go
D. Reserved resources
Correct Answer: D
Reserved resources, or Reserved Instances, are ideal for workloads with predictable usage and a long-term commitment, such as a minimum lifecycle of five years. This model allows for significant cost savings compared to on-demand pricing, and the instance is not ephemeral, meaning it persists and is dedicated to the user for the duration of the reservation. The licensing charged per physical CPU count aligns with dedicated host or reserved instance models, but the long- term commitment points more towards reserved resources.
Question 10:
Servers in the hot site are clustered with the main site.
A. Network traffic is balanced between the main site and hot site servers.
B. Offline server backups are replicated hourly from the main site.
C. All servers are replicated from the main site in an online status.
D. Which of the following best describes a characteristic of a hot site?
Correct Answer: C
When servers in a hot site are clustered with the main site, it indicates that all servers are replicated from the main site in an online status.
This means that the hot site maintains a live, real-time copy of data and applications, ensuring immediate availability in the event of a failure at the main site.
Unlike options A and B, which describe load balancing and backup strategies respectively, clustering with a hot site as described in option C ensures that the hot site can take over with minimal downtime, maintaining business continuity.
References: CompTIA Cloud+ CV0-004 Study Guide and Official CompTIA Content
Question 11:
A company has ten cloud engineers working on different manual following is the best method to address this issue?
A. Deployment documentation
B. Service logging
C. Configuration as code
D. Change ticketing
Correct Answer: C
Configuration as code is the best method to address the issue of cloud engineers working on different manual configurations.
This practice allows configurations to be scripted and automated, which reduces human error, enhances consistency, and makes the deployment process more efficient and reproducible.
References: Configuration as code is part of cloud deployment best practices, ensuring standardized environments, which is a key topic within the CompTIA Cloud+ curriculum.
Question 12:
A security engineer Identifies a vulnerability m a containerized application. The vulnerability can be exploited by a privileged process to read tie content of the host\’s memory. The security engineer reviews the following Dockerfile to determine a solution to mitigate similar exploits:
FROM alpine:3.17 RUN apk update andand apk upgrade COPY ./myapp ENTRYPOINT [“/myapp/app”]
Which of the following is the best solution to prevent similar exploits by privileged processes?
A. Adding the USER myappuserinstruction
B. Patching the host running the Docker daemon
C. Changing FROM alpiner3.17 to FROM alpine:latest
D. Running the container with the ready-only filesystem configuration
Correct Answer: A
Adding the “USER myappuser” instruction to the Dockerfile is the best solution to prevent similar exploits by privileged processes.
This instruction ensures that the container runs as a non-privileged user instead of the root user, significantly reducing the risk of privileged exploits. Running containers with least privilege principles minimizes the potential impact of vulnerabilities, enhancing the overall security posture of the containerized environment.
References: The CompTIA Cloud+ framework includes security concerns, measures, and concepts for cloud operations, highlighting the importance of container security practices, such as running containers as non-root users to prevent unauthorized access and exploitation.
Question 13:
A company wants to implement a work environment that will have low operational overhead and highly accessible enterprise resource planning, email, and data resources. Which of the following cloud service models should the company implement?
A. laaS
B. PaaS
C. DBaaS
D. SaaS
Correct Answer: D
A company that requires low operational overhead and highly accessible enterprise resources would benefit from implementing Software as a Service (SaaS).
SaaS provides access to applications hosted in the cloud, eliminating the need for internal infrastructure or application development, which aligns with the requirement of having low operational overhead. References: CompTIA Cloud+ Study Guide (V0-004) by Todd Montgomery and Stephen Olson
Question 14:
After accidentally uploading a password for an IAM user in plain text, which of the following should a cloud administrator do FIRST? (Choose two.)
A. Identify the resources that are accessible to the affected IAM user
B. Remove the published plain-text password
C. Notify users that a data breach has occurred
D. Change the affected IAM user\’s password
E. Delete the affected IAM user
Correct Answer: BD
The first step a cloud administrator should take after accidentally uploading a password for an IAM user in plain text is to remove the published plain-text password. This should be done immediately to prevent unauthorized access to the affected user\’s resources. The administrator should then change the password for the affected IAM user to a new, strong password. This will ensure that the user\’s resources are secure and that there is no unauthorized access.
A. Identifying the resources that are accessible to the affected IAM user is important, but it should not be done before removing the plain-text password and changing the password for the affected user. This step can be taken after the immediate security concerns have been addressed.
C. While it is important to notify users of a data breach, this step is not necessary in this situation as the password was accidentally uploaded and there is no evidence that any unauthorized access has occurred. However, the cloud administrator should review their security protocols to ensure that similar incidents do not occur in the future.
E. Deleting the affected IAM user is not necessary in this situation, as the user\’s resources can be secured by changing the password. Deleting the user may cause unnecessary disruption to the user\’s workflow and could result in the loss of important data.
In summary, the first step a cloud administrator should take after accidentally uploading a password for an IAM user in plain text is to remove the published plain-text password, followed by changing the password for the affected user.
Question 15:
An e-commerce store is preparing for an annual holiday sale. Previously, this sale has increased the number of transactions between two and ten times the normal level of transactions. A cloud administrator wants to implement a process to scale the web server seamlessly. The goal is to automate changes only when necessary and with minimal cost.
Which of the following scaling approaches should the administrator use?
A. Scale horizontally with additional web servers to provide redundancy.
B. Allow the load to trigger adjustments to the resources.
C. When traffic increases, adjust the resources using the cloud portal.
D. Schedule the environment to scale resources before the sale begins.
Correct Answer: B
To seamlessly scale the web server for an e-commerce store during an annual sale, it\’s best to allow the load to trigger adjustments to the resources. This approach uses autoscaling to automatically adjust the number of active servers based on the current load, ensuring an automated change that is cost-effective. References: CompTIA Cloud+ Study Guide (V0-004) – Chapter on Cloud Scalability
…
Ending
There are currently some suppliers on the Internet that provide CompTIA Cloud+ CV0-004 certification exam materials for free, but their question banks are not private, let alone the success rate. They collect books and past exam questions and distribute them on their own websites, so there is no It is recommended to spend time practicing on it.
Candidates spend about 3 days practicing 285 private CompTIA Cloud+ CV0-004 dumps exam questions according to the study pace of 2 hours a day: https://www.pass4itsure.com/cv0-004.html to ensure your success Pass the exam.
After passing the exam, remember to celebrate your achievement with everyone. You deserve it!